Setting up IP-Masquerading
ArticleCategory: [Es gibt verschiedene Artikel Kategorien]
System Administration
AuthorImage:[Ein Bild von Dir]
![[Photo of the Author]](../../common/images/Guido-S.gif)
TranslationInfo:[Author and translation history]
original in en Guido Socher
AboutTheAuthor:[Eine kleine Biographie über den Autor]
Guido is a long time Linux fan.
His Linux home page can be found at
www.oche.de/~bearix/g/.
Abstract:[Here you write a little summary]
IP-Masquerading provides the possibility to connect several computers
to the Internet using a computer running Linux with just one public IP address.
This means you can connect a whole private network to the Internet, and
your Internet Service provider thinks you are still connecting just
one single computer. This article will explain how to configure
IP-Masquerading with a 2.2.x Kernel. It does not explain how to build
a network. To get a general idea about computer networks I
recommend to read also the January 2000
issue article about home networks.
ArticleIllustration:[This is the title picture for your article]
![[Illustration]](../../common/images/illustration151.gif)
ArticleBody:[The article body]
General
To use IP-Masquerading as explained in this article you need
at least one Linux box with a 2.2.x Kernel. This machine is used
to set up the connection to the Internet. Using Linux as your
connection-sharing box doesn't mean that you have run Linux in your
internal network. In fact, Linux works well with Windows, Macs, and
other flavours of Unix.
This connection-sharing box is what we are concerned about in
this article. It connects on one side to the Internet and on the
other side to your private network. The machine has therefore
at least 2 interfaces and also at least 2 IP addresses. One of
the IP addresses is a public IP address which can be routed in the
Internet. This IP address is usually assigned to you by your Internet
Service Provider the very moment you setup your modem connection
(or what ever you use).
The other IP addresses is a private address which you can assign from
one of these ranges:
- 10.0.0.0 - 10.255.255.255
- 172.16.0.0 - 172.31.255.255
- 192.168.0.0 - 192.168.255.255 (we use this range in this article)
This article does not explain how to set up your network. I assume
that your private network is already in place and configured.
IP-Masquerading principles
Basically IP-Masquerading translates internal IP addresses
into external IP addresses. This is called network address translation
and Linux does this by using something called port-numbers.
From the outside world, all connections will seem to
be originating from your Linux box.
You can
find a detailed explanation in January issue.
Sometimes, IP packets are special in nature and
IP-Masquerading may not work for all applications, but it works in
most cases.
There are modules for ICQ, ftp, and quake that need to be inserted
in the Kernel in
order for those special applications to run correctly from the
internal network. In general though, anything that uses only the HTTP
(web browsers), telnet, ssh, or smtp (email) will work fine.
Setting up the Kernel
People who use an out of the box Kernel from one of the major
Linux distributions (Redhat, Mandrake, Debian, Suse...) can skip
this chapter as their kernel is already prepared to use IP-Masquerading.
I usually make a backup of /usr/src/linux/.config after I have
compiled a successfully working Kernel. Next time I need to compile
a Kernel I just load this configuration and I have already the configuration
of my previous Kernel in place. It is then relatively simple to configure
minor changes such as IP-Masquerading.
To use IP-Masquerading say yes to the following when configuring the
Kernel.
These are just the components you need for IP Masquerade, select
whatever other options you need for your specific setup.
- Prompt for development and/or incomplete code/drivers
CONFIG_EXPERIMENTAL
(this will allow you to select experimental IP Masquerade code compiled
into the kernel)
- Enable loadable module support
CONFIG_MODULES
- Networking support
CONFIG_NET
- Network firewalls
CONFIG_FIREWALL
- TCP/IP networking
CONFIG_INET
- IP: forwarding/gatewaying
CONFIG_IP_FORWARD
- IP: firewalling
CONFIG_IP_FIREWALL
- IP: masquerading
CONFIG_IP_MASQUERADE
- IP: ipportfw masq support
CONFIG_IP_MASQUERADE_IPPORTFW
- IP: ipautofw masquerade support
CONFIG_IP_MASQUERADE_IPAUTOFW
- IP: ICMP masquerading
CONFIG_IP_MASQUERADE_ICMP
- IP: always defragment
CONFIG_IP_ALWAYS_DEFRAG
- Dummy net driver support
CONFIG_DUMMY
- IP: ip fwmark masq-forwarding support
CONFIG_IP_MASQUERADE_MFW
Configure IP-Masquerading
We will write a little script to automate IP-Masquerading configuration.
You should
put the the following script into
/etc/rc.d/init.d/ and call it ipmasq. Change permissions
with chmod 755 ipmasq to make it executable.
The script below assumes that
you have used the static IP address 192.168.0.1 on the interface
towards your internal network (ifconfig eth0 192.168.0.1 netmask 255.255.255.0).
Please
change the script if you are using something else.
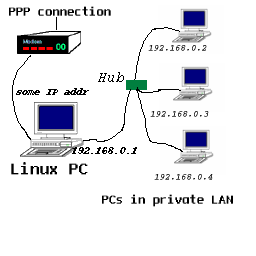
This picture shows the network plan of the network that we are using.
#!/bin/sh
echo "Setting up IP masquerading ..."
# People still using windows to surf the web must convert this
# to a UNIX text file before using it.
#
# Support masquerading of FTP file transfer.
/sbin/modprobe ip_masq_ftp
#
#--------------
# Note: the modules below are commented out from loading. Remove the
# comment sign if you want to use the corresponding applications form
# one of the computers inside your internal network.
#
# Support masquerading of RealAudio over UDP.
#/sbin/modprobe ip_masq_raudio
#
# Supports the masquerading of IRC DCC file transfers
#/sbin/modprobe ip_masq_irc
#
# Support masquerading of Quake and QuakeWorld
# Quake I / QuakeWorld (ports 26000 and 27000)
#/sbin/modprobe ip_masq_quake
#
# Quake I/II/III / QuakeWorld (ports 26000, 27000, 27910, 27960)
#/sbin/modprobe ip_masq_quake ports=26000,27000,27910,27960
#
# Support masquerading of the CuSeeme video conferencing software
#/sbin/modprobe ip_masq_cuseeme
#
#Support masquerading of the VDO-live video conferencing software
#/sbin/modprobe ip_masq_vdolive
#--------------
# Important: Enable IP forwarding. It is disabled by default in
# the 2.2.x Kernels
echo "1" > /proc/sys/net/ipv4/ip_forward
#
# NOTE: This is an example for an internal Network address of
# 192.168.0.x The sub netmask is 255.255.255.0 or "24" bit
# Please change this if you use different internal IP addresses.
#
/sbin/ipchains -P forward DENY
/sbin/ipchains -A forward -s 192.168.0.0/24 -j MASQ
#
#--- end of file
To test it make sure you have
configured all your
computers in your private network to have a default gateway route (!!!) to
192.168.0.1 (the masquerading Linux host).
Then run the script as root on the masquerading host.
After that send a ping from one machine
inside your network to a host in the Internet (e.g ping 213.239.9.21)
If this works then masquerading works. Try also
ping www.linuxfocus.org This should give the same
results as the above ping. If it does not work then check the
/etc/resolv.conf file on your clients. It should exist on every computer inside
your network and should list the DNS server of your ISP.
With Windows 9x-Clients you need to bind the network configuration of the
TCP/IP-Stack to the Networkcard and DNS needs to be activated by adding
the DNS server of the ISP under 'search order for DNS Server'.
Once the pings work everything else (e.g web browsing) will also work.
Now it is time to change your configuration
such that your /etc/rc.d/init.d/ipmasq script will be executed automatically
every time you boot your Linux connection-box. The best way to do this
is in my opinion to edit the /etc/rc.d/init.d/network file (this
file should already exist) and execute /etc/rc.d/init.d/ipmasq
AT THE END of the start section in the init.d/network file.
Look for a case statement and then for the "start)".
Conclusion
As you saw it is not difficult to setup IP-Masquerading.
It is basically just ip forwarding enabled and 2 ipchains commands.
IP-Masquerading is a very powerful application for small home networks
schools small business networks etc....
For further and more detailed information I recommend reading the
IP-Masquerading mini howto and the IPCHAINS-HOWTO.
To use IP-Masquerading you need to have of course a correctly configured
network. This is not covered by this article. The Home networking
article will give you some vocabulary and the Net 3 howto
or the The Network Administrator Guide explains in detail how to build a
network. I plan also to write an other article on networking later on
in the year but you might not want to wait that long :-).
![[Photo of the Author]](../../common/images/Guido-S.gif)
![[Illustration]](../../common/images/illustration151.gif)
