|
Oracle® Application Server Enterprise Deployment Guide
10g Release 2 (10.1.2) for Windows or UNIX B13998-03 |
|
 Previous |
 Next |
|
Oracle® Application Server Enterprise Deployment Guide
10g Release 2 (10.1.2) for Windows or UNIX B13998-03 |
|
 Previous |
 Next |
This appendix provides sample configurations for commonly used load balancers. It contains these sections:
Section A.1, "Test Network Configuration"
Section A.2, "F5 Big IP Application Switch (Software Version 4.5 PTF.5)"
Section A.3, "Cisco CSM 3.1(2)"
Section A.4, "Foundry Server Iron v08.1.00cT24"
Section A.5, "Nortel Alteon 2424 SSL (Software Version 20.2.2.1)"
Section A.6, "Radware Web Server Director NP with SynApps 7.50.05"
This section identifies the elements of the network configuration and considerations for the operation of Oracle Application Server components. Figure A-1 shows the configuration, its subnets, and the placement of the Oracle Application Server components in it.
The test network consists of several subnets for deployment of the hardware and Oracle Application Server components:
Internet
Simulated public network
Firewall-Load Balancer Transport Net
Network between the border firewall and load balancer external interface
DMZ or Web Tier
The OracleAS Single Sign-On middle tiers are installed on this tier. This subnet has two gateways:
Internal interface of the load balancer
Firewall interface to the data tier
Data Tier
The Oracle Application Server Infrastructure instance are installed on this tier. This is a protected network.
The test configuration contains the following hardware:
Check Point Firewall-1 NG internal firewall (DMZ to the Intranet)
One of the following load balancers (F5 Big IP was used in Oracle tests):
F5 Big IP Application Switch (Software Version 4.5 PTF.5)
Foundry Server Iron v08.1.00cT24
OracleAS Portal and OracleAS Wireless use server-to-server communication. This means that an OracleAS Portal or OracleAS Wireless instance must be able to make HTTP or HTTPS requests to a virtual IP address (VIP), and have the requests routed back to itself or another instance of its kind on the Web tier. The invalidation requests that OracleAS Portal makes to OracleAS Web Cache must be handled in a similar manner.
This section describes the communication in general terms and identifies the network configuration that enables it. For specific instructions on configuring a particular load balancer, refer to the section for that load balancer.
The Parallel Page Engine in OracleAS Portal makes loop-back (server-to-server) requests from the middle tier Oracle Application Server instance and back to that instance. In order to make OracleAS Portal highly available, these loop-back requests must be received by the load balancer, rather than individual Oracle Application Server middle tier instances.
After the Parallel Page Engine requests are routed to the VIP on the load balancer, the source address for the Parallel Page Engine requests must use Network Address Translation (NAT) to ensure correct routing. Without NAT on the source IP address of Parallel Page Engine requests, the host will respond directly to the client, which will break the session, since the client was expecting the response from the VIP. Figure A-2 shows how an address is translated after the request is processed by the load balancer.
Figure A-2 OracleAS Portal Parallel Page Engine Network Address Translation
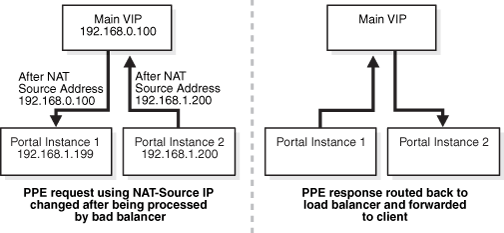
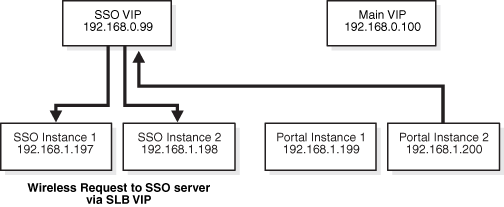
OracleAS Wireless makes requests to OracleAS Single Sign-On (which should be located with OracleAS Wireless on the Web tier). In order to make OracleAS Wireless highly available, these requests must be received by the load balancer. These requests must also processed by NAT, as the OracleAS Single Sign-On and OracleAS Portal instances reside on the same subnet.
Figure A-3 shows the request from the OracleAS Portal instance to the OracleAS Single Sign-On load balancer.
Figure A-3 Request Routing to the OracleAS Single Sign-On Server Load Balancer
OracleAS Portal also makes invalidation requests to OracleAS Web Cache. In order for the invalidation to function correctly, you must enable communication on port 9401 from the OracleAS Portal repository to a VIP that can communicate with the OracleAS Web Cache instances on the Web tier. Depending on how routing is configured in the network, you may also need to use NAT for these requests, and open outbound ports as needed on the data tier.
This section describes the network configuration necessary to test the Big IP Application Switch load balancer with the Oracle Application Server 10g Release 2 (10.1.2) application server.
The following subnets were used in the Big IP configuration:
External: 192.168.200.0/24 (DMZ2)
Internal: 192.168.0.0/24 (DMZ1)
Two interfaces were created:
1.1 192.168.200.5/24 (External)
1.2 192.168.0.1/24 (Internal)
|
Note: In the configuration for port 1.2, Secure Network Address Translation (SNAT) automap was also enabled. |
As shown in Figure A-1, "Test Network Configuration", the following servers were used for the middle tier installations and OracleAS Single Sign-On servers:
pdln-mid1.pdx.com
pdln-mid2.pdx.com
pdln-sso1.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
pdln-sso2.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
The following pools were created:
Pool 1: HTTP
pdln-mid1.pdx.com (Port 7777)
pdln-mid2.pdx.com (Port 7777)
Enable SNAT
Pool 2: OracleAS Single Sign-On
pdln-sso1.pdx.com (Port 7777)
pdln-sso2.pdx.com (Port 7777)
Enable SNAT
Persistent rebalance
Pool 3: OracleAS Web Cache Invalidation
pdln-mid1.pdx.com (Port 9401)
pdln-mid2.pdx.com (Port 9401)
Enable SNAT
The following load balancing methods were used:
Middle tiers: Round Robin with basic HTTP health check
Identity Management: Least Connections with OracleAS Single Sign-On health check (in-house)
You can create health monitors for Oracle Application Server components as described in this section.
Send String: GET /sso/status
Receive Rule: The OC4J_SECURITY instance is running
Since there are multiple components running on the middle tiers, the best way to monitor this is with an HTTP GET /. You can also create customized health checks using OracleAS Portal and OracleAS Wireless status pages.
A health monitor is needed for OracleAS Web Cache invalidation messages. Use HTTP LOGIN to monitor these messages.
Monitor Oracle Internet Directory LDAP communication using LDAP LOGIN.
Because two different hosts (sso-linux and linux) were used, two proxies, each with its own certificate, were created:
Proxy 1
Type: SSL
IP:Port: 192.168.200.10:443 (linux.pdx.com)
Destination Host: 192.168.200.10:80 (linux.pdx.com)
(Certificate information here)
Proxy 2
Type: SSL
IP:Port: 192.168.200.11:443 (sso-linux.pdx.com)
Destination Host: 192.168.200.11:80 (sso-linux.pdx.com)
(Certificate information here)
These proxies decrypt the HTTPS session in Big IP's internal SSL accelerator and forward the HTTP traffic back to the VIP.
In order to use the load balancer to handle the Parallel Page Engine requests from the middle tiers, you must set up Secure Network Address Translation (SNAT) on the VLAN's self IP address and the middle tier pools. To do this, follow the instructions in this section.
In the network configuration, check SNAT Automap for the self IP of the internal interface.
In the middle tier pool configuration, ensure that SNAT is enabled and NAT is disabled.
Issue the following command:
b vlan internal snat automap enable
In the preceding command, internal is the IP address of the internal interface.
Test the configuration with a telnet command from one of the middle tiers to the VIP address on port 80, with a HEAD request, for example:
telnet 192.168.200.10 80
HEAD
A response similar to the following should be returned:
Date: Wed, 02 Jun 2004 15:08:25 GMT
Allow: GET, HEAD
Server: OracleAS-Web-Cache-10g/10.1.2.0.0
Content-Type: text/html
Content-Length: 100
Cache-Control: public
Ensure that SNAT is enabled on the pool that was created for invalidation requests. You may also need to create a static route on the firewall to ensure that invalidation requests are routed properly. (This is required, since the middle tier may have a different route to the database.)
If you are using SSL and routing Parallel Page Engine and Invalidation requests though the load balancer/SSL accelerator, you must import the trusted site certificate. To do this, follow the instructions in the Oracle Application Server Portal Configuration Guide, section titled "Adding Certificates for Trusted Sites".
The configuration described in the preceding sections can also be applied to OracleAS Wireless. The only difference is that the middle tiers must know the IP address of the OracleAS Single Sign-On pool, and be able to route requests to that pool to authenticate clients. If you are using SSL, you must also import CA and Site certificates into the OracleAS Wireless configuration. See the Oracle Application Server Wireless Administrator's Guide for instructions.
If you are using OracleAS Web Cache with Big IP, ensure that the Big IP version is at least 4.5 PTF5, with the fix described in the F5 document 28154. Without this version and the fix, severe performance problems will occur. (In versions later than 4.5 PTF5, the problems have been fixed.)
This section describes the network configuration necessary to test the Cisco CSM 3.1(2) load balancer with the Oracle Application Server 10g Release 2 (10.1.2) application server.
The following subnets were used in the Cisco CSM 3.1(2) configuration:
External: 192.168.200.0/24 (DMZ2)
Internal: 192.168.0.0/24 (DMZ1)
As shown in Figure A-1, "Test Network Configuration", the following servers were used for the middle tier installations and OracleAS Single Sign-On servers:
pdln-mid1.pdx.com
pdln-mid2.pdx.com
pdln-sso1.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
pdln-sso2.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
The following VLANs were created:
VLAN 2: Client
VLAN 200: Server (Web tier)
VLAN 400: Server (SSL)
The following server farms were created:
HTTPS_POOL (Redirection to SSL Accelerator)
NAT server
No NAT client
Real 192.168.100.10
LINUX_FARM
NAT server
No NAT client
Real 192.168.0.104 7777
Real 192.168.0.105 7777
LINUX_FARM2
NAT server
NAT client SOURCENAT (for Parallel Page Engine requests)
Real 192.168.0.104 7777
Real 192.168.0.105 7777
SSO_FARM
NAT server
No NAT client
Real 192.168.0.101 7777
SSO FARM2
NAT server
NAT client SOURCENAT
Real 192.168.0.101
SSO_SSL-A (Redirection to SSL Accelerator)
NAT server
No NAT client
Real 192.168.100.11
WC_INVAL (Web Cache Invalidation)
NAT server
NAT client WEBCACHE (for NAT of invalidation requests)
Real 192.168.0.101 9401
Real 192.168.0.105 9401
This section describes the virtual servers in the Cisco CSM 3.1(2) configuration.
HTTPS_POOL (Redirect to SSL Accelerator)
Virtual 192.168.200.10 tcp https
Serverfarm HTTPS_POOL
Sticky 120 group 4
No persistent rebalance
HTTP_POOL (HTTP direct to servers)
Virtual 192.168.200.11 tcp https
VLAN 2
Serverfarm LINUX_FARM
Sticky 120 group 2
Idle 7200
Peristent rebalance
SSO3 (SSL redirection to the SSL Accelerator)
Virtual 192.168.200.11 tcp https
VLAN 2
Serverfarm SSO_SSL-A
Persistent rebalance
sticky 2 netmask 255.255.255.255 timeout 120
sticky 3 ssl timeout 120
sticky 4 netmask 255.255.255.255 timeout 120
HTTP_POOL3 (Accept requests from the SSL Accelerator VLAN to the middle tiers)
Virtual 192.168.200.10 tcp www
VLAN 400
Serverfarm LINUX_FARM
Persistent rebalance
SSO (Accepts HTTP requests from the SSL Accelerator VLAN to the SSO servers)
Virtual 192.168.200.11 tcp https
VLAN 400
Serverfarm SSO_FARM
Idle 7200
Persistent rebalance
HTTP-2 (Accept requests from the server VLAN for Parallel Page Engine loop-back)
Virtual 192.168.200.10 tcp www
VLAN 200
Serverfarm LINUX_FARM2
Persistent rebalance
In order to allow the wireless authentication using OracleAS Single Sign-On, the following virtual server must be created on the middle tier VLAN to allow communication from the OracleAS Portal middle tier to the OracleAS Single Sign-On server's VIP:
SSO2
Virtual 192.168.200.11 tcp https
VLAN 200
Serverfarm SSO_FARM2
Persistent rebalance
The following virtual server is required for OracleAS Web Cache invalidation:
WEBCACHE_INVAL
Virtual 192.168.200.10 tcp 9401
VLAN 200
Serverfarm WC_INVAL
Persistent rebalance
To verify the Parallel Page Engine communication from the middle tiers, follow these steps:
Test the configuration with a telnet command from one of the middle tiers to the VIP address on port 80, with a HEAD request, for example:
telnet 192.168.200.10 80
HEAD
A response similar to the following should be returned:
Date: Wed, 02 Jun 2004 15:08:25 GMT
Allow: GET, HEAD
Server: OracleAS-Web-Cache-10g/10.1.2.0.0
Content-Type: text/html
Content-Length: 100
Cache-Control: public
|
Note: You can perform the same test for the invalidation communication from the Infrastructure database. Syntax errors may occur with these requests, but if the response contains the preceding information, the communication is functioning properly. |
Current configuration : 8198 bytes ! ! Last configuration change at 01:03:50 PDT Tue May 18 2004 ! NVRAM config last updated at 01:03:52 PDT Tue May 18 2004 ! version 12.1 service timestamps debug datetime show-timezone service timestamps log datetime show-timezone no service password-encryption ! hostname pd-cat6k ! boot buffersize 522200 boot system slot0:c6sup22-jsv-mz.121-8a.EX boot bootldr bootflash:c6msfc2-boot-mz.121-8a.E5.bin enable secret 5 $1$u2be$MClIIqnBVnmCaNTtAMxLI/ ! clock timezone PST -8 clock summer-time PDT recurring clock calendar-valid redundancy main-cpu auto-sync standard diagnostic level complete ip subnet-zero ! ! no ip domain-lookup ! no mls ip multicast aggregate no mls ip multicast non-rpf cef mls qos statistics-export interval 300 mls qos statistics-export delimiter | module ContentSwitchingModule 3 vlan 2 client ip address 192.168.200.5 255.255.255.0 gateway 192.168.200.1 ! vlan 200 server ip address 192.168.0.1 255.255.255.0 ! vlan 400 server ip address 192.168.100.1 255.255.255.0 !! natpool WEBCACHE 192.168.200.125 192.168.200.125 netmask 255.255.255.0 natpool SOURCENAT 192.168.200.100 192.168.200.100 netmask 255.255.255.0 ! serverfarm HTTPS_POOL nat server no nat client real 192.168.100.10 inservice ! serverfarm LINUX_FARM nat server no nat client real 192.168.0.104 7777 inservice real 192.168.0.105 7777 inservice ! serverfarm LINUX_FARM2 nat server nat client SOURCENAT real 192.168.0.104 7777 inservice real 192.168.0.105 7777 inservice ! serverfarm SSO_FARM nat server no nat client real 192.168.0.100 7777 no inservice real 192.168.0.101 7777 inservice ! serverfarm SSO_FARM2 nat server nat client SOURCENAT real 192.168.0.101 7777 inservice ! serverfarm SSO_SSL-A nat server no nat client real 192.168.100.11 inservice ! serverfarm WC_INVAL nat server nat client WEBCACHE real 192.168.0.104 9401 inservice real 192.168.0.105 9401 inservice ! sticky 2 netmask 255.255.255.255 timeout 120 sticky 3 ssl timeout 120 sticky 4 netmask 255.255.255.255 timeout 120 ! vserver HTTP-2 virtual 192.168.200.10 tcp www vlan 200 serverfarm LINUX_FARM2 persistent rebalance inservice ! vserver HTTPS_POOL virtual 192.168.200.10 tcp https serverfarm HTTPS_POOL sticky 120 group 4 idle 7200 no persistent rebalance inservice ! vserver HTTP_POOL virtual 192.168.200.10 tcp www vlan 2 serverfarm LINUX_FARM sticky 120 group 4 idle 7200 persistent rebalance inservice ! vserver HTTP_POOL3 virtual 192.168.200.10 tcp www vlan 400 serverfarm LINUX_FARM persistent rebalance inservice ! vserver SSO virtual 192.168.200.11 tcp www vlan 400 serverfarm SSO_FARM idle 7200 persistent rebalance inservice ! vserver SSO2 virtual 192.168.200.11 tcp https vlan 200 serverfarm SSO_FARM2 persistent rebalance inservice ! vserver SSO3 virtual 192.168.200.11 tcp https vlan 2 serverfarm SSO_SSL-A persistent rebalance inservice ! vserver WEBCACHE_INVAL virtual 192.168.200.10 tcp 9401 vlan 200 serverfarm WC_INVAL persistent rebalance inservice ! ! ! ! interface GigabitEthernet1/1 no ip address shutdown ! interface GigabitEthernet1/2 no ip address shutdown ! interface FastEthernet2/1 (Management Interface) ip address 138.1.33.105 255.255.255.128 duplex full speed 100 ! interface FastEthernet2/2 no ip address duplex full speed 100 switchport switchport access vlan 2 switchport mode access ! interface FastEthernet2/3 no ip address duplex full speed 100 switchport switchport access vlan 200 switchport mode access ! interface FastEthernet2/4 no ip address duplex full speed 100 switchport switchport access vlan 400 switchport mode access ! interface FastEthernet2/5 no ip address duplex full speed 100 switchport switchport access vlan 400 switchport mode access ! interface FastEthernet2/6 no ip address duplex full speed 100 switchport switchport access vlan 400 switchport mode access ! interface FastEthernet2/7 no ip address duplex full speed 100 switchport switchport access vlan 400 switchport mode access ! interface FastEthernet2/8 no ip address duplex full speed 100 switchport switchport access vlan 400 switchport mode access ! interface FastEthernet2/9 no ip address duplex full speed 100 switchport switchport access vlan 400 switchport mode access ! interface FastEthernet2/10 no ip address duplex full speed 100 switchport switchport access vlan 400 switchport mode access ! interface FastEthernet2/11 no ip address duplex full speed 100 switchport switchport access vlan 200 switchport mode access ! interface FastEthernet2/12 no ip address duplex full speed 100 switchport switchport access vlan 200 switchport mode access ! interface FastEthernet2/13 no ip address duplex full speed 100 switchport switchport access vlan 200 switchport mode access ! interface FastEthernet2/14 no ip address duplex full speed 100 switchport switchport access vlan 200 switchport mode access ! interface Vlan1 no ip address shutdown ! ! interface Vlan200 no ip address ! ip default-gateway 138.1.34.229 ip classless no ip http server ! ! tftp-server slot0:c6slb-apc.2-1-1.bin ! line con 0 line vty 0 4 password welcome login transport input lat pad mop telnet rlogin udptn nasi ! end pd-cat6k#
This section describes the network configuration necessary to test the Foundry Server Iron v08.1.00cT24 load balancer with the Oracle Application Server 10g Release 2 (10.1.2) application server.
The following subnets were used in the Foundry Server Iron v08.1.00cT24 configuration:
External: 192.168.200.0/24 (DMZ2)
Internal: 192.168.0.0/24 (DMZ1)
As shown in Figure A-1, "Test Network Configuration", the following servers were used for the middle tier installations and OracleAS Single Sign-On servers:
pdln-mid1.pdx.com
pdln-mid2.pdx.com
pdln-cache1.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
pdln-cache2.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
Server103 192.168.0.105 (OracleAS Portal on pdln.mid1)
Source-NAT
Port 7777
Port 9401
Server102 192.168.0.104 (OracleAS Portal on pdln-mid2)
Source-NAT
Port 7777
Port 9401
Server101 192.168.200.101 (Identity Management and OracleAS Single Sign-On middle tier on pdln-cache1)
Port 7777
To verify the Parallel Page Engine communication from the middle tiers, follow these steps:
Test the configuration with a telnet command from one of the middle tiers to the VIP address on port 80, with a HEAD request, for example:
telnet 192.168.200.10 80
HEAD
A response similar to the following should be returned:
Date: Wed, 02 Jun 2004 15:08:25 GMT
Allow: GET, HEAD
Server: OracleAS-Web-Cache-10g/10.1.2.0.0
Content-Type: text/html
Content-Length: 100
Cache-Control: public
|
Note: You can perform the same test for the invalidation communication from the Infrastructure database. Syntax errors may occur with these requests, but if the response contains the preceding information, the communication is functioning properly. |
In order for invalidation to work correctly, you must ensure that client NAT is enabled on each of the real servers on which OracleAS Web Cache is installed. You may also need to create a static route on the firewall to ensure that invalidation requests are routed properly.
If you are using SSL and routing Parallel Page Engine and Invalidation requests though the load balancer/SSL accelerator, you must import the trusted site certificate. To do this, follow the instructions in the Oracle Application Server Portal Configuration Guide, section titled "Adding Certificates for Trusted Sites".
The configuration described in the preceding sections can also be applied to OracleAS Wireless. The only difference is that the middle tiers must know the IP address of the OracleAS Single Sign-On pool, and be able to route requests to that pool to authenticate clients. If you are using SSL, you must also import CA and Site certificates into the OracleAS Wireless configuration. See the Oracle Application Server Wireless Administrator's Guide for instructions.
ver 08.1.00cT24 ! module 1 bi-0-port-wsm-management-module module 2 bi-8-port-gig-copper-module module 4 bi-24-port-copper-module ! global-protocol-vlan ! ! ! ! ! server real server103 192.168.0.105 source-nat port 7777 port 9401 ! server real server102 192.168.0.104 source-nat port 7777 port 9401 port 7778 ! server real server101 192.168.0.101 source-nat port 7777 ! server cache-name ssl_10 192.168.100.10 port http port http no-health-check port http url "HEAD /" port ssl port ssl no-health-check ! server cache-name ssl_11 192.168.100.11 port http port http no-health-check port http url "HEAD /" port ssl port ssl no-health-check ! server real server100 192.168.0.100 source-nat port 7777 ! ! server virtual 200_10 192.168.200.10 sym-priority 254 port http port http spoofing port 9401 port 7778 port ssl sticky bind http server102 7777 server103 7777 bind 9401 server102 9401 server103 9401 bind ssl ssl_10 ssl ! server virtual 200_11 192.168.200.11 sym-priority 254 port http port http spoofing port ssl sticky bind http server100 7777 bind ssl ssl_11 ssl ! server vip-group 1 vip 192.168.200.10 vip 192.168.200.11 server cache-group 1 cache-name ssl_10 cache-name ssl_11 ! ! vlan 1 name DEFAULT-VLAN by port ! vlan 4092 name internal by port untagged ethe 2/5 to 2/8 ethe 4/13 to 4/18 ethe 4/23 to 4/24 router-interface ve 1 ! vlan 4093 name external by port untagged ethe 2/1 to 2/4 ethe 4/1 to 4/12 router-interface ve 2 ! vlan 4095 name SSL by port untagged ethe 4/19 to 4/21 router-interface ve 3 ! ! hostname ServerIron_1 ip default-network 192.168.200.1/24 ip l4-policy 1 cache tcp 0 global ip l4-policy 2 cache tcp ssl global ip route 0.0.0.0 0.0.0.0 192.168.200.1 ip route 192.168.2.0 255.255.255.0 192.168.0.200 ! username twillard password ..... router vrrp snmp-server community ..... rw ! interface ethernet 2/1 confirm-port-up 6 ! interface ethernet 2/2 confirm-port-up 6 ! interface ethernet 2/3 confirm-port-up 6 ! interface ethernet 2/4 confirm-port-up 6 ! interface ethernet 2/5 confirm-port-up 6 ! interface ethernet 2/6 confirm-port-up 6 ! interface ethernet 2/7 confirm-port-up 6 ! interface ethernet 2/8 confirm-port-up 6 ! interface ethernet 4/1 speed-duplex 100-full ! interface ethernet 4/13 speed-duplex 100-full ! interface ve 1 ip address 192.168.0.1 255.255.255.0 ip vrrp vrid 1 owner advertise backup ip-address 192.168.0.1 vip-group 1 track-port ve 2 activate ! interface ve 2 ip address 192.168.200.5 255.255.255.0 ip vrrp vrid 2 owner advertise backup ip-address 192.168.200.5 track-port ve 1 activate ! interface ve 3 ip address 192.168.100.1 255.255.255.0 ip vrrp vrid 3 owner advertise backup ip-address 192.168.100.1 track-port ve 1 activate ! ! ! ! end
This section describes the network configuration necessary to test the Nortel Alteon 2424 SSL (Software Version 20.2.2.1) load balancer with the Oracle Application Server 10g Release 2 (10.1.2) application server.
The following subnets were used in the Foundry Server Iron v08.1.00cT24 configuration:
External: 192.168.200.0/24 (DMZ2)
Internal: 192.168.0.0/24 (DMZ1)
As shown in Figure A-1, "Test Network Configuration", the following servers were used for the middle tier installations and OracleAS Single Sign-On servers:
pdln-mid1.pdx.com
pdln-mid2.pdx.com
pdln-sso1.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
pdln-sso2.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
You must create Real Server entries for each middle tier balanced by the load balancer. Table A-2 lists the servers used in the test configuration.
The servers listed in Table A-2 must belong to groups, as listed in Table A-3. Note that the groups contain like instances, for example, Group 1 contains OracleAS Portal instances, Group 4 contains the Identity Management instances, and Group 5 has only the SSL accelerator.
This section describes the virtual IP addresses used in this configuration.
Virtual #1 is set up to listen on port 80 (HTTP) using the address 192.168.200.10, which is on the external subnet interface. Group 1 is bound to this virtual address, and the remote port 7777 (the OracleAS Web Cache listen port) has also been set. Pbind is for client stickiness; since we are using an OracleAS Web Cache cluster in this scenario, no real session binding is needed on the load balancer.
Virtual #4 is for OracleAS Single Sign-On, and is also configured on port 80 (can be set to 443 for SSL communication), using the address 192.168.200.11, which is on the external subnet interface. Group 4 is bound to this virtual server and the remote port 7777. No session binding is needed for the OracleAS Single Sign-On requests, but for his instance client IP has been selected.
To make the OracleAS Portal Parallel Page Engine and invalidation to work correctly, you must enable a proxy on the internal or server ports of the load balancer. This causes NAT (with PIP addresses) on any requests that are generated by the internal servers.
PIP Configuration: Configure PIP addresses that the proxy will use: For example:
/c/slb/pip<#>xxx.xxx.xxx.xxx
Replace the xs in the preceding example with the PIP address. The PIP addresses must be on the same subnet as the servers.
Port Configuration:
Port 1 (External): client enable, proxy enable
Port 2 (Internal server): client enable, proxy enable, server enable
Ports 3-8: client enable
In order for invalidation to work correctly, you must ensure that client NAT is enabled on each of the real servers on which OracleAS Web Cache is installed. You may also need to create a static route on the firewall to ensure that invalidation requests are routed properly.
If you are using SSL and routing Parallel Page Engine and Invalidation requests though the load balancer/SSL accelerator, you must import the trusted site certificate. To do this, follow the instructions in the Oracle Application Server Portal Configuration Guide, section titled "Adding Certificates for Trusted Sites".
The configuration described in the preceding sections can also be applied to OracleAS Wireless. The only difference is that the middle tiers must know the IP address of the OracleAS Single Sign-On pool, and be able to route requests to that pool to authenticate clients. If you are using SSL, you must also import CA and Site certificates into the OracleAS Wireless configuration. See the Oracle Application Server Wireless Administrator's Guide for instructions.
script start "Alteon Application Switch 2424-SSL" 4 /**** DO NOT EDIT THIS LINE!
/* Configuration dump taken 10:47:15 Thu Jun 3, 2004
/* Version 20.2.2.1, Base MAC address 00:01:81:2e:b8:50
/c/sys
http ena
/c/sslproc/
mip 192.168.100.15
rts ena
/c/port 1
pvid 2
/c/port 1/fast
speed 100
fctl none
mode full
auto off
/c/port 2
pvid 3
/c/port 2/fast
speed 100
fctl none
mode full
auto off
/c/port 3
pvid 2
/c/port 3/fast
speed 100
fctl both
mode full
auto on
/c/port 4
pvid 4
/c/port 4/fast
speed 100
fctl both
mode full
auto on
/c/port 5
pvid 4
/c/port 5/fast
speed 100
fctl both
mode full
auto on
/c/port 6
pvid 4
/c/port 6/fast
speed 100
fctl both
mode full
auto on
/c/port 7
pvid 4
/c/port 7/fast
speed 100
fctl both
mode full
auto on
/c/port 8
pvid 4
/c/port 8/fast
speed 100
fctl both
mode full
auto on
/c/port 9
tag ena
pvid 4
/c/port 9/fast
speed any
fctl both
mode full
auto on
/c/vlan 1
def 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28
/c/vlan 2
ena
name "Outside-Virtual"
def 1 3
/c/vlan 3
ena
name "DMZ"
def 2
/c/vlan 4
ena
name "SSL"
def 4 5 6 7 8 9
/c/vlan 99
ena
name "VLAN 99"
def 0
/c/stp 1/off
/c/stp 1/clear
/c/stp 1/add 1 2 3 4 99
/c/ip/if 1
ena
addr 192.168.200.5
vlan 2
/c/ip/if 2
ena
addr 192.168.0.1
vlan 3
/c/ip/if 3
ena
addr 192.168.100.1
vlan 4090
/c/ip/gw 1
ena
addr 192.168.200.1
retry 1
/c/ip/route
add 192.168.2.0 255.255.255.0 192.168.0.200 2
/c/slb
on
/c/slb/adv
direct ena
/c/slb/real 1
ena
rip 192.168.0.104
inter 15
retry 6
/c/slb/real 2
ena
rip 192.168.0.105
inter 15
retry 6
/c/slb/real 3
ena
rip 192.168.0.100
inter 15
retry 6
/c/slb/real 4
dis
rip 192.168.0.101
inter 15
retry 6
/c/slb/real 5
ena
rip 192.168.100.10
/c/slb/group 1
metric roundrobin
add 1
add 2
/c/slb/group 2
metric roundrobin
/c/slb/group 4
metric roundrobin
add 3
add 4
/c/slb/group 5
health sslh
add 5
/c/slb/pip/pip1 192.168.0.150
/c/slb/pip/pip2 192.168.0.151
/c/slb/pip/pip3 192.168.0.152
/c/slb/pip/pip4 192.168.0.153
/c/slb/port 1
client ena
proxy ena
/c/slb/port 2
client ena
server ena
proxy ena
/c/slb/port 3
client ena
/c/slb/port 4
client ena
/c/slb/port 5
client ena
/c/slb/port 6
client ena
/c/slb/port 7
client ena
/c/slb/port 8
client ena
/c/slb/virt 1
ena
vip 192.168.200.10
dname "linux.pdx.com"
/c/slb/virt 1/service http
group 1
rport 7777
pbind clientip
/c/slb/virt 1/service 9401
group 1
/c/slb/virt 4
ena
vip 192.168.200.11
dname "sso-linux.pdx.com"
/c/slb/virt 4/service http
group 4
rport 7777
pbind clientip
/c/slb/virt 2/service 443/pbind sslid
/c/slb/filt 5
ena
action redir
proto tcp
dport https
group 5
rport 0
vlan any
/c/slb/port 1
filt ena
add 5
/c/slb/port 2
filt ena
add 5
/
script end /**** DO NOT EDIT THIS LINE!
SSL Configuration:
SSL >> Configuration# dump
Dump private keys (yes/no) [no]: no
Collecting data, please wait...
/*
/*
/* Configuration dump taken Tue Aug 3 12:54:14 PDT 2004
/* Version 4.1.2.3
/*
/*
/*
/cfg/.
/cfg/ssl/.
/cfg/ssl/dns/.
cachesize 1000
retransmit 2s
count 3
ttl 3h
health 10s
hdown 2
hup 2
fallthrough off
/cfg/ssl/cert 1/.
name PDCQA-CA
cert
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
...
/cfg/ssl/cert 1/revoke/.
/cfg/ssl/cert 1/revoke/automatic/.
interval 1d
ena disabled
/cfg/ssl/cert 2/.
name linux.pdx.com
cert
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
...
/cfg/ssl/cert 2/revoke/.
/cfg/ssl/cert 2/revoke/automatic/.
interval 1d
ena disabled
/cfg/ssl/cert 4/.
name sso-linux.pdx.com
cert
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
...
/cfg/ssl/cert 4/revoke/.
/cfg/ssl/cert 4/revoke/automatic/.
interval 1d
ena disabled
/cfg/ssl/server 1/.
name linux.pdx.com
vip 192.168.200.10
port "443 (https)"
rip 0.0.0.0
rport "80 (http)"
type http
proxy off
ena enabled
/cfg/ssl/server 1/trace/.
/cfg/ssl/server 1/ssl/.
cert 2
cachesize 9400
cachettl 5m
cacerts 1
cachain 1
protocol ssl3
verify none
ciphers ALL@STRENGTH
ena enabled
/cfg/ssl/server 1/tcp/.
cwrite 15m
ckeep 15m
swrite 15m
sconnect 10s
csendbuf auto
crecbuf auto
ssendbuf auto
srecbuf 6000
/cfg/ssl/server 1/http/.
redirect on
sslheader on
addxfor off
addvia on
addxisd off
addfront off
addclicert off
addbeassl off
addbeacli off
addnostore off
cmsie shut
rhost off
maxrcount 40
maxline 8192
/cfg/ssl/server 1/http/rewrite/.
rewrite off
ciphers HIGH:MEDIUM
response iSD
URI "/cgi-bin/weakcipher"
/cfg/ssl/server 1/http/auth/.
mode basic
realm Xnet
proxy off
ena disabled
/cfg/ssl/server 1/dns/.
/cfg/ssl/server 1/adv/.
/cfg/ssl/server 1/adv/pool/.
timeout 15s
ena disabled
/cfg/ssl/server 1/adv/traflog/.
sysloghost 0.0.0.0
udpport 514
priority info
facility local4
ena disabled
/cfg/ssl/server 1/adv/standalone/.
ena disabled
/cfg/ssl/server 1/adv/standalone/iplist/.
/cfg/ssl/server 1/adv/loadbalancing/.
type all
persistence none
metric hash
health auto
interval 10s
ena disabled
/cfg/ssl/server 1/adv/loadbalancing/script/.
/cfg/ssl/server 1/adv/loadbalancing/remotessl/.
protocol ssl3
ciphers ALL
/cfg/ssl/server 1/adv/loadbalancing/remotessl/verify/.
verify none
/cfg/ssl/server 1/adv/sslconnect/.
protocol ssl3
ciphers EXP-RC4-MD5:ALL!DH
ena disabled
/cfg/ssl/server 1/adv/sslconnect/verify/.
verify none
/cfg/ssl/server 4/.
Name sso-linux.pdx.com
vip 192.168.200.11
port "443 (https)"
rip 0.0.0.0
rport "80 (http)"
type generic
proxy off
ena enabled
/cfg/ssl/server 4/trace/.
/cfg/ssl/server 4/ssl/.
cert 4
cachesize 9400
cachettl 5m
protocol ssl3
verify none
ciphers ALL@STRENGTH
ena enabled
/cfg/ssl/server 4/tcp/.
cwrite 15m
ckeep 15m
swrite 15m
sconnect 10s
csendbuf auto
crecbuf auto
ssendbuf auto
srecbuf 6000
/cfg/ssl/server 4/adv/.
/cfg/ssl/server 4/adv/standalone/.
ena disabled
/cfg/ssl/server 4/adv/standalone/iplist/.
/cfg/ssl/server 4/adv/loadbalancing/.
type all
persistence none
metric hash
health auto
interval 10s
ena disabled
/cfg/ssl/server 4/adv/loadbalancing/script/.
/cfg/ssl/server 4/adv/loadbalancing/remotessl/.
protocol ssl3
ciphers ALL
/cfg/ssl/server 4/adv/loadbalancing/remotessl/verify/.
verify none
/cfg/ssl/server 4/adv/sslconnect/.
protocol ssl3
ciphers EXP-RC4-MD5:ALL!DH
ena disabled
/cfg/ssl/server 4/adv/sslconnect/verify/.
verify none
/cfg/xnet/.
ttl 15m
log login
/cfg/sys/.
/cfg/sys/routes/.
/cfg/sys/time/.
tzone "America/Los_Angeles"
/cfg/sys/time/ntp/.
/cfg/sys/dns/.
/cfg/sys/syslog/.
/cfg/sys/cluster/.
mip 192.168.100.15
/cfg/sys/cluster/host 1/.
type master
ip 192.168.100.10
gateway 192.168.100.1
/cfg/sys/cluster/host 1/routes/.
/cfg/sys/cluster/host 1/interface 1/.
ip 192.168.100.10
netmask 255.255.255.0
vlanid 0
mode failover
primary 0
/cfg/sys/cluster/host 1/interface 1/ports/.
add 1
/cfg/sys/accesslist/.
/cfg/sys/adm/.
clitimeout 10m
telnet off
ssh off
/cfg/sys/adm/snmp/.
/cfg/sys/adm/snmp/snmpv2-mib/.
snmpEnableAuthenTraps disabled
/cfg/sys/adm/snmp/community/.
read public
trap trap
/cfg/sys/adm/audit/.
vendorid "1872 (alteon)"
vendortype 2
ena false
/cfg/sys/adm/audit/servers/.
/cfg/sys/adm/http/.
port 80
ena false
/cfg/sys/adm/https/.
port 443
ena false
/cfg/sys/user/.
expire 0
This section describes the network configuration necessary to test the Radware Web Server Director NP load balancer with the Oracle Application Server 10g Release 2 (10.1.2) application server.
The following subnets were used in the Foundry Server Iron v08.1.00cT24 configuration:
External: 192.168.200.0/24 (DMZ2)
Internal: 192.168.0.0/24 (DMZ1)
As shown in Figure A-1, "Test Network Configuration", the following servers were used for the middle tier installations and OracleAS Single Sign-On servers:
pdln-mid1.pdx.com
pdln-mid2.pdx.com
pdln-sso1.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
pdln-sso2.pdx.com (Identity Management, OracleAS Single Sign-On middle tier)
The following farms were created for the Radware Web Server Director NP Configuration:
Farm 1: 192.168.0.150 HTTP
Farm 2: 192.168.0.151 OracleAS Web Cache invalidation
Farm 3: 192.168.0.152 OracleAS Single Sign-On
Farm 4: 192.168.0.153 CT100 — linux.pdx.com
Farm 5: 192.168.0.154 CT100 — sso-linux.pdx.com
Table A-2 lists the servers used in the test configuration.
Table A-5 Servers
| Farm Address | Server Address | Name | Multiplexed Server Port |
|---|---|---|---|
|
192.168.0.150 |
192.168.0.104 |
pdln-mid2 |
7777 |
|
192.168.0.150 |
192.168.0.105 |
pdln-mid1 |
7777 |
|
192.168.0.151 |
192.168.0.104 |
pdln-mid2 |
7777 |
|
192.168.0.151 |
192.168.0.105 |
pdln-mid2 |
7777 |
|
192.168.0.152 |
192.168.0.100 |
pdln-sso1 (OracleAS Single Sign-On) |
7777 |
|
192.168.0.152 |
192.168.0.101 |
pdln-sso2 (OracleAS Single Sign-On) |
7777 |
|
192.168.0.153 |
192.168.100.10 |
CT100 (linux.pdx.com) |
7777 |
|
192.168.0.154 |
|
CT100 (sso-linux.pdx.com) |
7777 |
The following additional configuration is necessary for the Radware Web Server Director NP:
Enable client NAT. Do not specify any address under Use Specific NAT Address.
Specify the NAT address range to use.
Specify the client addresses for NAT:
192.168.0.104 - 192.168.0.105 for middle tier
192.168.2.100 - 192.168.2.100 for Infrastructure invalidation requests.
Specify client NAT Enable in the server configuration.
Table A-6 lists the super farms for the Radware Web Server Director NP configuration:
Table A-6 Super Farms
| IP Address | Port Number | Farm Address | Function |
|---|---|---|---|
|
192.168.200.10 |
80 |
192.168.0.150 |
linux.pdx.com HTTP |
|
192.168.200.10 |
443 |
192.168.0.153 |
linux.pdx.com HTTPS --> CT100 |
|
192.168.200.10 |
9401 |
192.168.0.151 |
Invalidation VIP |
|
192.168.200.11 |
80 |
192.168.0.152 |
OracleAS Single Sign-On HTTP |
|
192.168.200.11 |
443 |
192.168.0.154 |
OracleAS Single Sign-On HTTPS --> CT100 |
The following load balancing methods were used:
Middle tiers: Cyclic with HTTP health check on port 7777
Identity Management: Cyclic with HTTP health check on port 7777
To verify the Parallel Page Engine communication from the middle tiers, follow these steps:
Test the configuration with a telnet command from one of the middle tiers to the VIP address on port 80, with a HEAD request, for example:
telnet 192.168.200.10 80
HEAD
A response similar to the following should be returned:
Date: Wed, 02 Jun 2004 15:08:25 GMT
Allow: GET, HEAD
Server: OracleAS-Web-Cache-10g/10.1.2.0.0
Content-Type: text/html
Content-Length: 100
Cache-Control: public
|
Note: You can perform the same test for the invalidation communication from the Infrastructure database. Syntax errors may occur with these requests, but if the response contains the preceding information, the communication is functioning properly. |
In order for invalidation to work correctly, you must ensure that client NAT is enabled on each of the real servers on which OracleAS Web Cache is installed. You may also need to create a static route on the firewall to ensure that invalidation requests are routed properly.
If you are using SSL and routing Parallel Page Engine and Invalidation requests though the load balancer/SSL accelerator, you must import the trusted site certificate. To do this, follow the instructions in the Oracle Application Server Portal Configuration Guide, section titled "Adding Certificates for Trusted Sites".
The configuration described in the preceding sections can also be applied to OracleAS Wireless. The only difference is that the middle tiers must know the IP address of the OracleAS Single Sign-On pool, and be able to route requests to that pool to authenticate clients. If you are using SSL, you must also import CA and Site certificates into the OracleAS Wireless configuration. See the Oracle Application Server Wireless Administrator's Guide for instructions.
system config ! !Device Configuration !Date: 15-06-2004 21:44:33 !Device Description: Web Server Director NP with SynApps !Base MAC Address: 00:03:b2:0d:43:c0 !Software Version: 7.50.05 (build 49dee4) ! net route table cdbset 192.168.4.2 255.255.255.255 192.168.0.200 net route table cdbset 192.168.2.0 255.255.255.0 192.168.0.200 net route table cdbset 0.0.0.0 0.0.0.0 192.168.200.1 manage snmp community-table cdbset 0.0.0.0 public -ca super -st trapsEnable system tune bridge-fft-table cdbset 1024 system tune ip-fft-table cdbset 8192 system tune arp-table cdbset 1024 system tune client-table cdbset 16384 system tune routing-table cdbset 512 wsd farm table cdbset 192.168.0.151 WCACHE_INVAL -as enable wsd farm table cdbset 192.168.0.154 CT100-SSO -as enable -dm cyclic -cp 443 wsd farm table cdbset 192.168.0.154 CT100-SSO -as enable -dm cyclic -cp 443 wsd farm table cdbset 192.168.0.153 CT100 -as enable -dm cyclic -cp 443 wsd farm table cdbset 192.168.0.153 CT100 -as enable -dm cyclic -cp 443 wsd farm table cdbset 192.168.0.150 HTTP -as enable -dm cyclic -cp 7777 wsd farm table cdbset 192.168.0.150 HTTP -as enable -dm cyclic -cp 7777 wsd farm table cdbset 192.168.0.152 SSO -as enable -dm cyclic -cp 7777 wsd farm table cdbset 192.168.0.152 SSO -as enable -dm cyclic -cp 7777 wsd farm table cdbset 192.168.0.151 WCACHE_INVAL -as enable -dm cyclic wsd farm table cdbset 192.168.0.151 WCACHE_INVAL -as enable -dm cyclic wsd farm table cdbset 192.168.0.151 WCACHE_INVAL -as enable -dm cyclic wsd farm server table cdbset 192.168.0.154 192.168.100.11 ct100-sso wsd farm server table cdbset 192.168.0.153 192.168.100.10 CT100 wsd farm server table cdbset 192.168.0.150 192.168.0.105 pdln-mid1 wsd farm server table cdbset 192.168.0.150 192.168.0.104 pdln-mid2 wsd farm server table cdbset 192.168.0.152 192.168.0.100 pdln-cache1 wsd farm server table cdbset 192.168.0.151 192.168.0.105 pdln-mid1 wsd farm server table cdbset 192.168.0.151 192.168.0.104 pdln-mid2 wsd physical-server statistics cdbset pdln-cache1 wsd physical-server statistics cdbset pdln-mid2 wsd physical-server statistics cdbset ct100-sso wsd physical-server statistics cdbset CT100 wsd physical-server statistics cdbset pdln-mid1 wsd super-farm cdbset 192.168.200.11 443 192.168.0.154 wsd super-farm cdbset 192.168.200.10 443 192.168.0.153 wsd super-farm cdbset 192.168.200.11 80 192.168.0.152 wsd super-farm cdbset 192.168.200.10 80 192.168.0.150 wsd super-farm cdbset 192.168.200.10 9401 192.168.0.151 wsd nat server status cdbset disable system tune dynamic-proximity-table cdbset 4096 wsd farm connectivity-check httpcode cdbset 192.168.0.154 200 wsd farm connectivity-check httpcode cdbset 192.168.0.153 200 wsd farm connectivity-check httpcode cdbset 192.168.0.152 200 wsd farm connectivity-check httpcode cdbset 192.168.0.150 200 wsd farm connectivity-check httpcode cdbset 192.168.0.151 200 wsd nat server specific-nat-address cdbset 0.0.0.0 system tune url-table cdbset 256 system tune request-table cdbset 200 system tune ssl-id-table cdbset 1024 net next-hop-router cdbset 192.168.200.1 net next-hop-router cdbset 138.1.34.229 wsd farm nhr cdbset 0.0.0.0 -ip 192.168.200.1 wsd farm extended-params cdbset 192.168.0.150 net ip-interface cdbset 192.168.200.5 255.255.255.0 2 net ip-interface cdbset 192.168.100.1 255.255.255.0 16 net ip-interface cdbset 192.168.0.1 255.255.255.0 1 wsd nat client address-range cdbset 192.168.0.25 -t 192.168.0.25 wsd nat client range-to-nat cdbset 192.168.2.100 -t 192.168.2.155 wsd nat client range-to-nat cdbset 192.168.0.100 -t 192.168.0.105 wsd nat client status cdbset enable system tune nat-address-table cdbset 1 system tune nat-ports-table cdbset 64512 bwm modify policy cdbset Default -i 0 -dst any -src any bwm modify policy cdbset Default -i 0 -dst any -src any -dr oneway health-monitoring response-level-samples cdbset 0 manage user table cdbset radware -pw radware manage telnet status cdbset enable manage web status cdbset enable manage ssh status cdbset enable manage secure-web status cdbset enable net physical-interface cdbset 1 -s fe100 -d full -a on net physical-interface cdbset 2 -s fe100 -d full wsd#