 | Chapter 5 The sendmail.cf File |  |
The other commands in a configuration file tend to be more complex than the version command you just saw (so complex, in fact, that whole chapters are dedicated to most of them). Here, we present a quick tour of each command - just enough to give you the flavor of a configuration file but in small enough bites to be easily digested.
Recall that the sendmail program does not generally deliver mail itself.
Instead, it calls other programs to perform that delivery.
The M command defines a mail delivery
agent (a program that delivers
the mail). For example, as was
previously shown:
Mlocal, P=/bin/mail, F=lsDFMAw5:/|@rmn, S=10, R=20/40,
This tells sendmail that local
mail is to be delivered by using the /bin/mail program.
The other parameters in this line are introduced in Chapter 6, The Mail Hub and Delivery Agents,
and detailed in
Chapter 30, Delivery Agents.
The ability to define a value once and then use it
in many places makes maintaining your sendmail.cf file easier.
The D sendmail.cf command defines a macro.
A macro's name is either a single letter or curly-brace-enclosed
multiple characters. It has text as a value. Once
defined, that text can be referenced symbolically elsewhere:
DRmail.us.edua single letter D{REMOTE}mail.us.edu
multiple characters (beginning with V8.7)
Here, R and {REMOTE} are macro names that have the
string mail.us.edu as their values. Those values are accessed
elsewhere in the sendmail.cf file with expressions such as
$R and ${REMOTE}.
Macros are introduced in
Chapter 7, Macros,
and detailed in
Chapter 31, Defined Macros.
At the heart of the sendmail.cf file are sequences of rules that
rewrite (transform) mail addresses from one form to another.
This is necessary chiefly because addresses must conform to many
differing standards. The R command is used to define a rewriting rule:
R$- $@ $1 @ $R user -> user @ remote
Mail addresses are compared to the rule on
the left ($-). If they match that rule, they are rewritten on the basis of the rule on the right ($@ $1 $@ $R). The text at the far
right is a comment (that doesn't require a leading #).
Use of multicharacter macros and # comments can make rules
appear a bit less cryptic:
R$- # If a plain user name
$@ $1 @ ${REMOTE} # append "@" remote hostThe details of rules like this are more fully explained beginning in Chapter 8, Addresses and Rules, and detailed in Chapter 28, Rules.
Because rewriting may require several steps, rules are
organized into sets, which can be thought of as subroutines.
The S command begins a rule set:
S3
This particular S command begins rule set
3. Beginning with V8.7 sendmail, rule sets
can be given symbolic names as well as numbers:
SHubset
This particular S command begins a rule set
named Hubset.
[3]
Named rule sets are automatically assigned
numbers by sendmail.
[3] This is an actual symbolic name that we will use when developing the client.cf file (specifically in Chapter 11, Rule Sets 1 and S=).
All the R commands (rules) that follow an S command
belong to that rule set.
A rule set ends when another S command appears to
define another rule set.
Rule sets are introduced in
Chapter 8
and detailed in
Chapter 29, Rule Sets.
There are times when the single text value of a D command
(macro definition) is not sufficient. Often, you will want to
define a macro to have multiple values and view those values as
elements in an array.
The C command defines a class macro.
A class macro is like an array in that it can hold many items.
The name of a class is either a single letter or, beginning with
V8.7, a curly-brace-enclosed multicharacter name:
CW localhost fontservera single letter C{MY_NAMES} localhost fontserver
multiple characters (beginning with V8.7)
Here, each contains two items: localhost
and fontserver.
The value of a class macro is accessed
with an expression such as $=W or $={MY_NAMES}.
Class macros are introduced in
Chapter 12, Class,
and detailed in
Chapter 32, Class Macros.
To make administration easier, it is often convenient to store
long or volatile lists of values in a file.
The F sendmail.cf command defines a file class macro.
It is just like the C command above, except that the
array values are taken from a file:
FW/etc/mynames
F{MY_NAMES}/etc/mynames 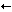 multiple characters (beginning with V8.7)
multiple characters (beginning with V8.7)Here, the file class macros W and {MY_NAMES} obtain their values
from the file /etc/mynames.
The file class macro can also take its list of values from the output of a program. That form looks like this:
FM|/bin/shownames
F{MY_NAMES}|/bin/shownames 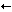 multiple characters (beginning with V8.7)
multiple characters (beginning with V8.7)Here, sendmail runs the program /bin/shownames.
The output of that program is appended to the class macro.
File class macros are introduced in
Chapter 12,
and detailed in
Chapter 32.
Options tell the sendmail program many useful and necessary things. They specify the location of key files, set timeouts, and define how sendmail will act and how it will dispose of errors. They can be used to tune sendmail to meet your particular needs.
The O command is used to set sendmail
options. An example of the option command looks like this:
OQ/var/spool/mqueue O QueueDirectory= /var/spool/mqueuebeginning with V8.7
Here, Q option (beginning with V8.7 called QueueDirectory) defines
the name of the directory in which mail will
be queued as /var/spool/mqueue.
Options are introduced in
Chapter 13, Setting Options,
and detailed in
Chapter 34, Options.
Mail messages are composed of two parts: a header followed (after
a blank line) by the body. The body may contain virtually anything.
[4]
The header, on the other hand, contains lines
of information that must strictly conform to certain standards.
The H command
is used to specify
which mail headers to include
in a mail message and how each will look:
[4] With the advent of MIME (Multipurpose Internet Mail Extensions), the message body can now be composed of many minimessages, each with its own MIME header and sub-body.
HReceived: $?sfrom $s $.by $j ($v/$Z)$?r with $r$. id $i$?u for $u$.; $b
This particular H command tells sendmail
that a Received:
header line must be added to the header of every mail message.
Headers are introduced in
Chapter 14, Headers, Precedence, and Trust,
and detailed in
Chapter 35, Headers.
Not all mail has the same priority. Mass mailings (to a
mailing list, for example) should be transmitted after mail to
individual users.
The P command sets the beginning priority
for a mail message. That priority is used to determine a
message's order when the mail queue is processed.
Pjunk= -100
This particular P command
tells sendmail that mail with a Precedence: header line
of junk should be processed last.
Priority commands are introduced in
Chapter 14
and detailed in
Chapter 35.
For some software (such as UUCP) to function correctly, it must be able
to tell sendmail whom a mail message is from.
This is necessary when that software runs as a different user
identity (uid) than that specified in the From:
line in the message header.
The T sendmail.cf command
[5]
lists those users that
are trusted to override the From: address in a mail
message.
All other users have a warning included in the mail message header.
[5] The
Tcommand was ignored from versions V8.1 through V8.6 and restored under V8.7. With V8.7 it is actually implemented as the class$=t.
Troot daemon uucp
This particular T sendmail.cf command says that there
are three users who are to be considered trusted. They are
root (who is a god under UNIX),
daemon (sendmail usually runs as the pseudo-user daemon),
and uucp (necessary for UUCP software
to work properly).
Trusted users are introduced in
Chapter 14
and detailed in
Chapter 22, Security.
Certain information, such as a list of UUCP hosts, is better maintained
outside of the sendmail.cf file.
External databases (called keyed databases) provide faster
access to such information. Keyed databases were introduced with V8.6 and
come in several forms, the nature and location of which are declared
with the K configuration command:
Kuucp hash /etc/mail/uucphosts
This particular K command declares a database with the
symbolic name uucp, with the type hash, located
in /etc/mail/uucphosts. The K command
is detailed and the types of databases are explained, in
Chapter 33, Database Macros.
The sendmail program is ultraparanoid about security. One way
to circumvent security with suid programs like sendmail is
by running them with bogus environmental variables. To prevent such
an end run, V8 sendmail erases all its environment variables
when it starts. It then presets the values for a small set
of variables (such as TZ and SYSTYPE). This small, safe environment
is then passed to its delivery agents.
Beginning with V8.7 sendmail,
sites that wish to augment this list may do so with the E
configuration command.
EPOSTGRESHOME=/home/postgres
Here, the environment variable POSTGRESHOME is assigned the value
/home/postgres. This allows programs to use the postgres(1)
database to access information.
The E command is detailed in
Chapter 22.