|
Oracle® Application Server Enterprise Deployment Guide
10g Release 2 (10.1.2) for Windows or UNIX B13998-03 |
|
 Previous |
 Next |
|
Oracle® Application Server Enterprise Deployment Guide
10g Release 2 (10.1.2) for Windows or UNIX B13998-03 |
|
 Previous |
 Next |
This chapter introduces Oracle Application Server installation types and architectures and the nomenclature used in this guide to describe the Enterprise Deployment architectures.
Oracle Application Server 10g Release 2 (10.1.2) is a complete, fully integrated product that delivers a wide range of solutions to business and technology challenges. This guide presents a subset of these, in the form of recommendations based on deployments by Oracle customers.
This guide provides installation and configuration steps for the following installation types and selections:
Oracle Identity Management
J2EE
OracleAS Portal
Business Intelligence and Forms
For complete descriptions of the components comprising these installation types and selections, see the Oracle Application Server Concepts guide.
The naming convention for the components and computers is established in the architecture diagrams and is used throughout this guide. Server names and their related URLs and IP addresses are provided in Table 2-1. The external load balancer nomenclature is provided in Table 2-2.
Table 2-1 Server Name, URL and IP Address Reference
| Description | Name | URL | IP Address |
|---|---|---|---|
|
Servers with 2-node Real Application Clusters database for Security Metadata Repository |
INFRADBHOST2 |
infradbhost1.mycompany.com infradbhost2.mycompany.com |
xxx.xxxx.xxx.225 xxx.xxxx.xxx.226 |
|
Servers with 2-node Real Application Clusters database for Application Metadata Repository |
APPDBHOST2 |
appdbhost1.mycompany.com appdbhost2.mycompany.com |
xxx.xxxx.xxx.227 xxx.xxxx.xxx.228 |
|
OIDHOST2 |
oidhost1.mycompany.com oidhost2.mycompany.com |
xxx.xxx.xxx.229 xxx.xxx.xxx.230 |
|
|
IDMHOST2 |
idmhost1.mycompany.com idmhost2.mycompany.com |
xxx.xxx.xxx.231 xxx.xxx.xxx.232 |
|
|
APPHOST2 |
apphost1.mycompany.com apphost2.mycompany.com |
xxx.xxx.xxx.233 xxx.xxx.xxx.234 |
|
|
WEBHOST2 |
webhost1.mycompany.com webhost2.mycompany.com |
xxx.xxx.xxx.235 xxx.xxx.xxx.236 |
Table 2-2 External Load Balancer Name, URL and IP Address Reference
This section briefly describes the Enterprise Deployment architectures in this guide, including minimum hardware requirements and a diagram of the architecture.
Figure 2-1 shows the enterprise deployment architecture for any J2EE application that uses JAZN LDAP for user authentication. If you need to use the Single Sign-On Server for authentication for J2EE applications, you should use the Standard Enterprise Deployment for Portal Applications: myPortalCompany.com described in Section 2.3.2, "myPortal".
For certain types of J2EE applications, such as JMS-based or EJB-based applications, there may be additional variants to these architectures. Refer to the Oracle Application Server Containers for J2EE Services Guide and Oracle Application Server Containers for J2EE Enterprise JavaBeans Developer's Guide for more information on these variants.
The servers in the myJ2EECompany system are grouped into tiers as follows:
Web Tier — WEBHOST1 and WEBHOST2, with Oracle HTTP Server installed.
Application Tier — APPHOST1 and APPHOST2, with Oracle Application Server Containers for J2EE installed, and multiple OC4J instances with applications deployed.
Data Tier — OIDHOST1 and OIDHOST2, with Oracle Internet Directory installed, and INFRADBHOST1 and INFRADBHOST2, the two-node Real Application Clusters database.
Table 2-3, Table 2-4 and Table 2-5 identify the basic, minimum hardware requirements for the servers in the myJ2EECompany system on Windows, Linux and Solaris operating systems, respectively. The memory figures represent the memory required to install and run Oracle Application Server; however, for most production sites, you should configure at least 1 GB of physical memory.
For detailed requirements, or for requirements for a platform other than these, see the Oracle Application Server Installation Guide for the platform you are using.
Table 2-3 myJ2EECompany Hardware Requirements (Windows)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
WEBHOST and APPHOST |
300 MHz or higher Intel Pentium processor recommended |
400 MB |
512 MB |
55 MB to run the installer; 256 MB needed for some installation types |
512 MB |
|
OIDHOST and INFRADBHOST |
300 MHz or higher Intel Pentium processor recommended |
2.5 GB |
1 GB |
55 MB to run the installer; 256 MB needed for some installation types |
1 GB |
Table 2-4 myJ2EECompany Hardware Requirements (Linux)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
WEBHOST and APPHOST |
Pentium (32-bit), 450 MHz or greater |
520 MB |
512 MB |
400 MB |
1.5 GB |
|
OIDHOST and INFRADBHOST |
Pentium (32-bit), 450 MHz or greater |
2.5 GB |
1 GB |
400 MB |
1.5 GB |
Table 2-5 myJ2EECompany Hardware Requirements (Solaris)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
WEBHOST and APPHOST |
450 MHz or greater; Oracle recommends a multiple CPU computer |
750 MB |
512 MB |
250 MB |
1.5 GB |
|
OIDHOST |
450 MHz or greater; Oracle recommends a multiple CPU computer |
1.54 GB |
1 GB |
250 MB |
1.5 GB |
|
INFRADBHOST |
450 MHz or greater; Oracle recommends a multiple CPU computer |
3.93 GB |
1 GB |
250 MB |
1.5 GB |
Figure 2-1 Enterprise Deployment Architecture for myJ2EECompany.com
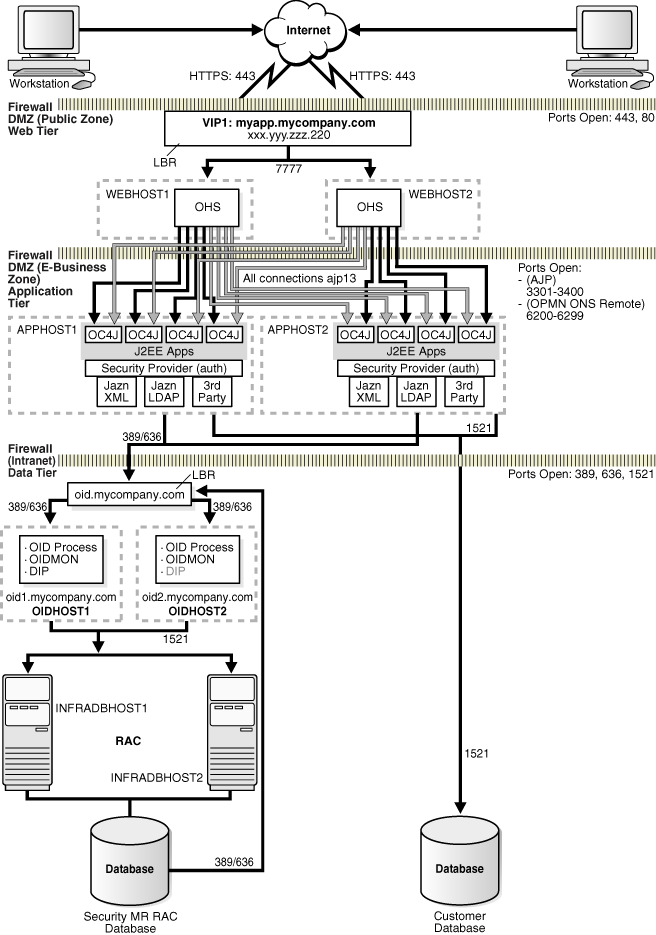
Figure 2-2 shows the enterprise deployment architecture for OracleAS Portal applications.
The servers in the myPortalCompany system are grouped into tiers as follows:
Application Tier — APPHOST1 and APPHOST2
Identity Management Tier — IDMHOST1 and IDMHOST2
Data Tier — OIDHOST1 and OIDHOST2, with Oracle Internet Directory installed, and INFRADBHOST1 and INFRADBHOST2, the two-node Real Application Clusters database. APPDBHOST1 and APPDBHOST2 contain the OracleAS Portal application metadata repository.
Table 2-6, Table 2-7 and Table 2-8 identify the basic, minimum hardware requirements for the servers in the myPortalCompany system on Windows, Linux and Solaris operating systems, respectively. The memory figures represent the memory required to install and run Oracle Application Server; however, for most production sites, you should configure at least 1 GB of physical memory. Table 2-9 describes the servers used in the Oracle test environment for myPortalCompany.
For detailed requirements, or for requirements for a platform other than these, see the Oracle Application Server Installation Guide for the platform you are using.
Table 2-6 myPortalCompany Hardware Requirements (Windows)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
APPHOST, IDMHOST, OIDHOST, INFRADBHOST, and APPDBHOST |
300 MHz or higher Intel Pentium processor recommended |
2.5 GB |
1 GB |
55 MB to run the installer; 256 MB needed for some installation types |
1 GB |
Table 2-7 myPortalCompany Hardware Requirements (Linux)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
APPHOST, IDMHOST, OIDHOST, INFRADBHOST, and APPDBHOST |
Pentium (32-bit), 450 MHz or greater |
2.5 GB |
1 GB |
400 MB |
1.5 GB |
Table 2-8 myPortalCompany Hardware Requirements (Solaris)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
APPHOST, IDMHOST, OIDHOST, INFRADBHOST, and APPDBHOST |
450 MHz or greater; Oracle recommends a multiple CPU computer |
750 MB |
512 MB |
250 MB |
1.5 GB |
Figure 2-2 Enterprise Deployment Architecture for myPortalCompany.com
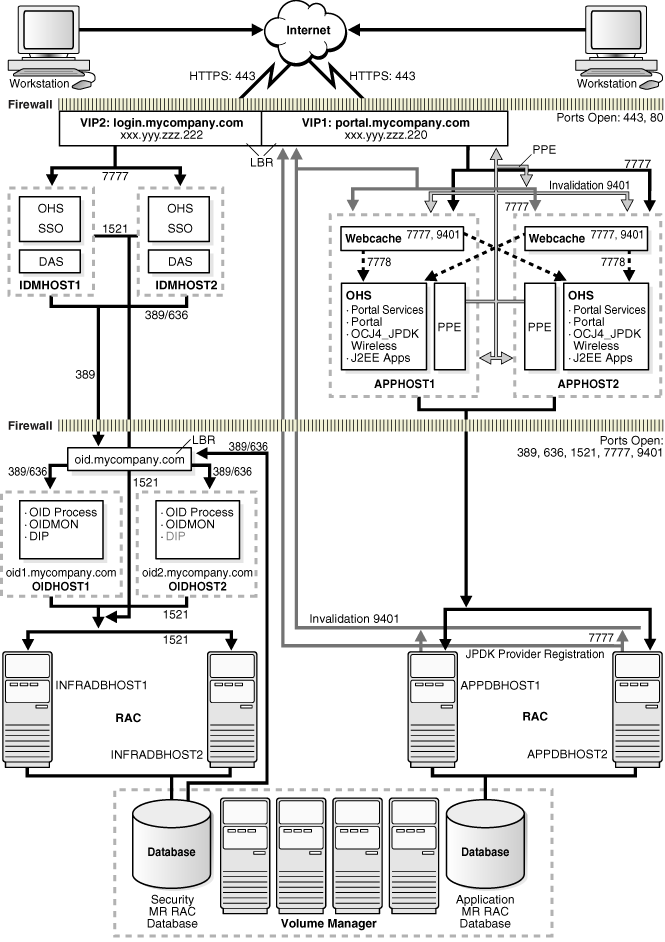
Table 2-9 myPortalCompany Servers in Oracle Test Environment
| Server | Platform | Virtual Memory | TMP | RAM | CPU |
|---|---|---|---|---|---|
|
INFRADBHOST1 and INFRADBHOST2 |
Windows 2000 |
2 GB |
Not applicable |
2 GB |
3 GHz |
|
OIDHOST1 |
Windows 2000 |
3 GB |
Not applicable |
2 GB |
3 GHz |
|
OIDHOST2 |
Windows 2000 |
2GB |
Not applicable |
2 GB |
3 GHz |
|
IDMHOST1 and IDMHOST2 |
Windows 2000 |
2 GB |
Not applicable |
3.75 GB |
3 GHz |
|
APPDBHOST1 and APPHOST2 |
Red Hat Linux 2.1 |
2 GB |
2.5 GB |
6 GB |
4 CPU, 3 GHz |
|
APPHOST1 and APPHOST2 |
Windows 2000 |
1.6 GB |
Not applicable |
3.75 GB |
3 GHz |
Figure 2-3 shows the enterprise deployment architecture for Oracle Business Intelligence and Forms applications.
The servers in the myBIFCompany system are grouped into tiers as follows:
Application Tier — APPHOST1 and APPHOST2
Identity Management Tier — IDMHOST1 and IDMHOST2
Data Tier — OIDHOST1 and OIDHOST2, with Oracle Internet Directory installed, and INFRADBHOST1 and INFRADBHOST2, the two-node Real Application Clusters database. APPDBHOST1 and APPDBHOST2 contain the OracleAS Portal application metadata repository.
Table 2-10, Table 2-11 and Table 2-12 identify the basic, minimum hardware requirements for the servers in the myBIFCompany system on Windows, Linux and Solaris operating systems, respectively. The memory figures represent the memory required to install and run Oracle Application Server; however, for most production sites, you should configure at least 1 GB of physical memory. Table 2-13 describes the servers used in the Oracle test environment for myBIFCompany.
For detailed requirements, or for requirements for a platform other than these, see the Oracle Application Server Installation Guide for the platform you are using.
Table 2-10 myBIFCompany Hardware Requirements (Windows)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
APPHOST, IDMHOST, OIDHOST, INFRADBHOST, and APPDBHOST |
300 MHz or higher Intel Pentium processor recommended |
2.5 GB |
1 GB |
55 MB to run the installer; 256 MB needed for some installation types |
1 GB |
Table 2-11 myBIFCompany Hardware Requirements (Linux)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
APPHOST, IDMHOST, OIDHOST, INFRADBHOST, and APPDBHOST |
Pentium (32-bit), 450 MHz or greater |
2.5 GB |
1 GB |
400 MB |
1.5 GB |
Table 2-12 myBIFCompany Hardware Requirements (Solaris)
| Server | Processor | Disk | Memory | TMP Directory | Swap |
|---|---|---|---|---|---|
|
APPHOST, IDMHOST, OIDHOST, INFRADBHOST and APPDBHOST |
450 MHz or greater; Oracle recommends a multiple CPU computer |
750 MB |
512 MB |
250 MB |
1.5 GB |
Figure 2-3 Enterprise Deployment Architecture for myBIFCompany.com
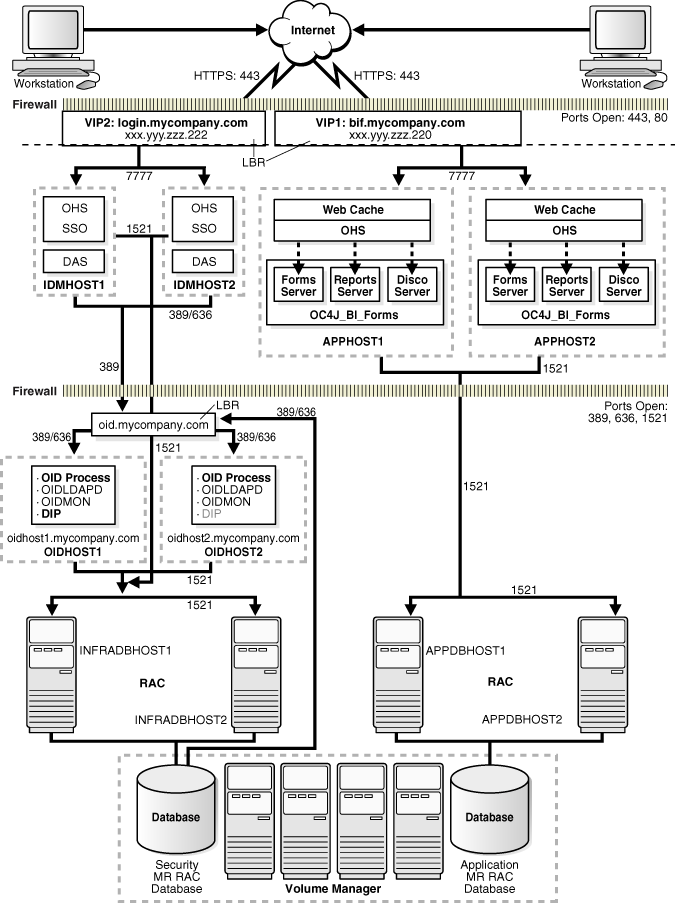
Table 2-13 myBIFCompany Servers in Oracle Test Environment
| Server | Platform | Virtual Memory | TMP | RAM | CPU |
|---|---|---|---|---|---|
|
INFRADBHOST1 and INFRADBHOST2 |
Windows 2000 |
2 GB |
Not applicable |
2 GB |
3 GHz |
|
OIDHOST1 |
Windows 2000 |
3 GB |
Not applicable |
2 GB |
3 GHz |
|
OIDHOST2 |
Windows 2000 |
2GB |
Not applicable |
2 GB |
3 GHz |
|
IDMHOST1 and IDMHOST2 |
Windows 2000 |
2 GB |
Not applicable |
3.75 GB |
3 GHz |
|
APPDBHOST1 and APPHOST2 |
Red Hat Linux 2.1 |
2 GB |
2.5 GB |
6 GB |
4 CPU, 3 GHz |
|
APPHOST1 and APPHOST2 |
Windows 2000 |
1.6 GB |
Not applicable |
3.75 GB |
3 GHz |
Figure 2-1, "Enterprise Deployment Architecture for myJ2EECompany.com", Figure 2-2, "Enterprise Deployment Architecture for myPortalCompany.com" and Figure 2-3, "Enterprise Deployment Architecture for myBIFCompany.com" show standard enterprise deployment architectures. Some characteristics of the standard enterprise deployment configuration are:
A two-node Real Application Clusters (RAC) database on the Data Tier is used to provide high availability (multiple database instances access a shared database of data files).
Oracle Internet Directory is installed on the Data Tier.
OracleAS Single Sign-On (on the Identity Management tier Figure 2-2), or the Oracle Application Server Java Authentication and Authorization Service (JAAS) Provider (on the Application Tier in Figure 2-1), is used for authentication and authorization.
Several variants exist for these and other elements of the enterprise deployment architectures. They are described in this section, categorized by the tier on which they are implemented (Data, Identity Management, Application, or Web). The variants enable you to achieve your deployment goals using fewer servers, different software, or alternative configurations.
This section describes the variants for the Data Tier. The Data Tier is depicted in Figure 2-2, "Enterprise Deployment Architecture for myPortalCompany.com", and comprises the INFRADBHOST1 and INFRADBHOST2 computers.
Multimaster replication is an Oracle Internet Directory software solution that ensures read and write access to Oracle Internet Directory at all times, if at least one of the computers in the system remains available. When a computer resumes functioning after unavailability, replication from the surviving computer resumes automatically and synchronizes the contents between the computers. In addition, changes made on one directory server instance are reflected on the second directory server instance.
Multimaster replication of Oracle Internet Directory differs from the standard configuration in that the Oracle Internet Directory server and the database are on the same computer, whereas in the standard configuration the first Oracle Internet Directory instance and a database instance occupy IDMHOST1 and INFRADBHOST1, while the second Oracle Internet Directory instance and a database instance occupy IDMHOST2 and INFRADBHOST2. Thus, the replicated Oracle Internet Directory operates two fewer servers than the RAC configuration.
To implement multimaster replication in Oracle Internet Directory, follow the instructions in the Oracle Internet Directory Administrator's Guide, Oracle Internet Directory Replication Administration chapter, section titled "Installing and Configuring Multimaster Replication".
The OracleAS Cold Failover Cluster (Identity Management) solution is a hardware cluster comprising two computers. The computer that is actively executing an Infrastructure installation at any given time is called the primary (hot) node. If this node fails, the hardware cluster automatically diverts Infrastructure operations to the secondary (cold) node.
Each hardware cluster node is a standalone server that runs its own set of processes, but accesses a shared storage subsystem. The cluster can access the same storage, usually disks, from both nodes, but only the primary node has active access to the storage at any given time. If the primary node fails, the hardware cluster's software grants the secondary node access to the storage.
|
Note: For a detailed discussion of the OracleAS Cold Failover Cluster (Identity Management) solution, see the Oracle Application Server High Availability Guide |
The OracleAS Cold Failover Cluster (Identity Management) solution differs from the standard configuration in the following ways:
The Oracle Internet Directory server and the database are on the same computer, whereas in the standard configuration the first Oracle Internet Directory instance and a database instance occupy IDMHOST1 and INFRADBHOST1, while the second Oracle Internet Directory instance and a database instance occupy IDMHOST2 and INFRADBHOST2. Thus, the OracleAS Cold Failover Cluster (Identity Management) solution operates two fewer servers than the RAC configuration.
In the event of node failure, clients will experience a brief interruption of service while the workload is diverted to the cold node.
To implement the OracleAS Cold Failover Cluster (Identity Management) solution:
Obtain and configure a hardware cluster.
Install and configure the Oracle Application Server instances on the cluster computers to use the OracleAS Cold Failover Cluster (Identity Management) solution. Follow the instructions in the Oracle Application Server Installation Guide, section 11.5, "Installing an OracleAS Cold Failover Cluster (Identity Management) Configuration".
Manage the OracleAS Cold Failover Cluster (Identity Management) solution, following the instructions from the Oracle Application Server High Availability Guide, section 6.3, "Managing Oracle Application Server Cold Failover Cluster (Identity Management)".
This section describes the variants for the Identity Management Tier. The Identity Management Tier is depicted in Figure 2-2, "Enterprise Deployment Architecture for myPortalCompany.com", and comprises the IDMHOST1 and IDMHOST2 computers.
Oracle Internet Directory can be installed on the Identity Management Tier, along with OracleAS Single Sign-On and Oracle Delegated Administration Services. This is typical of configurations that provide a complete, local identity management system (Oracle Internet Directory and Oracle Application Server Single Sign-On) on one computer to applications located near that computer. See the Oracle Identity Management Concepts and Deployment Planning Guide, Chapter 3, "Oracle Identity Management Deployment Planning", section titled "Planning the Physical Network Topologies".
In the standard configuration, in which Oracle Internet Directory is installed on the Data Tier, Oracle Internet Directory and its metadata repository are behind a firewall, and is isolated from Internet traffic.
Oracle Identity Management provides a set of components for integrating with other identity management environments, including various services and APIs, preconfigured directory connectivity solutions and standards support. For example, Oracle Identity Management allows for integration with various 3rd party directories, including Microsoft Active Directory and SunONE Directory Server.
By default, Oracle Directory Integration and Provisioning is installed as a component of Oracle Internet Directory. However, you can also install Oracle Directory Integration and Provisioning in a standalone installation. You should install a standalone instance of Oracle Directory Integration and Provisioning under the following circumstances:
When you need Oracle Internet Directory to run on a separate host for performance reasons
When the applications that you need to provision and synchronize required intensive processing
You need to run multiple instances of Oracle Directory Integration and Provisioning for high availability
See the Oracle Identity Management Integration Guide for detailed information on configuration options.
Several third-party access management vendors provide authentication adapters for the OracleAS Single Sign-On server. These products enable you to integrate a third-party system with the Oracle system without having to write your own code.The link that follows provides information about these vendors' products. All of the vendors listed certify that their products work with OracleAS Single Sign-On. See the section Single Sign-On under the heading Documentation, which appears near the bottom of the page.
http://www.oracle.com/technology/products/id_mgmt/partners/index.html
For example, Netegrity provides Siteminder Agent for Oracle Application Server. The agent delivers a mechanism to enable integration between heterogeneous, enterprise wide SiteMinder implementation with the OracleAS Single Sign-On environment. The agent provides enhanced security to protect Oracle Web-based resources, including session synchronization and revalidation of the user's SiteMinder session behind the DMZ in a trusted zone or corporate internal network prior to initiating the Oracle session. For the current information on version, platform support and configuration guide, visit:
Windows native authentication is an authentication scheme for those who use Internet Explorer on Windows platforms. When this feature is enabled in OracleAS Single Sign-On, users log in to single sign-on partner applications automatically using Kerberos credentials obtained when the user logs in to a Windows computer. Using the Simple Protected GSS-API Negotiation Protocol (SPNEGO), browsers that are Internet Explorer 5.0 and greater can automatically pass the user's Kerberos credentials to a Kerberos-enabled Web server when the server requests these credentials. The Web server can then decrypt the credentials and authenticate the user.Before setting up Windows native authentication, you must first set up Active Directory (AD) Synchronization to Oracle Internet Directory. See the Oracle Internet Directory Administrator's Guide for instructions on how to do this.
This section describes the variants for the Application Tier. The Application Tier is depicted in Figure 2-1, "Enterprise Deployment Architecture for myJ2EECompany.com", Figure 2-2, "Enterprise Deployment Architecture for myPortalCompany.com", and Figure 2-3, "Enterprise Deployment Architecture for myBIFCompany.com"and comprises the APPHOST1 and APPHOST2 computers.
An Oracle Application Server Farm is a collection of instances that share the same configuration management metadata repository. A farm can be either a Oracle Application Server File-Based Farm or Oracle Application Server Database-Based Farm. Within these farm types, there are three types of metadata repository configuration: File-based (with standalone instance), File-based (with repository host instance) and Database:
File-based repository (standalone instance) — Every instance includes a local file- based repository. In a standalone instance, this repository stores the configuration metadata for the instance. When an instance is part of an OracleAS Database-Based Farm or an OracleAS File-Based Farm, and the instance is not the repository host, the local file-based repository contains the Bill of Materials (BOM) that Distributed Configuration Management uses to validate that the instance is synchronized with the configuration metadata in the repository.
File-based repository (with repository host instance) — When an instance is defined as the repository host for an OracleAS File-Based Farm, the repository for the instance contains the configuration metadata for all instances in the farm.
Database repository - comprised of DCM schema. Storing the metadata repository in a database may be useful as part of a site's high availability and backup strategy. Using a database repository, the database serves as the repository host.
In all three metadata repository scenarios (database repository, file-based repository with a standalone instance, or file-based repository host instance), an instance always has a local file based repository. If the instance is not included in a farm, this is the sole storage for the configuration metadata for the instance.The choice of database repository or file-based repository has a low impact on a system's availability. In case of repository failure or downtime, the J2EE cluster continues to operate. Only the distributed management features are unavailable during the repository downtime. Table 2-14 compares repository types in light of operational considerations.
Table 2-14 OracleAS File-Based Farm and OracleAS Database-Based Farm Comparison
This section describes the variants for the Web Server Tier. The Web Server Tier is depicted in Figure 2-2, "Enterprise Deployment Architecture for myPortalCompany.com", and comprises the APPHOST1 and APPHOST2 computers.
In Figure 2-1, "Enterprise Deployment Architecture for myJ2EECompany.com", the Web Server Tier comprises the WEBHOST1 and WEBHOST2 computers.
OracleAS Web Cache is a content-aware server accelerator, or reverse proxy server, that improves the performance, scalability, and availability of Web sites that run on Oracle Application Server. Oracle recommends configuring multiple instances of OracleAS Web Cache to run as members of a cache cluster. A cache cluster is a loosely coupled collection of cooperating OracleAS Web Cache cache instances that provide a single logical cache.When deploying topologies described in this document, one variant is to place OracleAS Web Cache on a separate host. This is particularly useful in environments with large amounts of cacheable content. This architecture modification provides flexibility in choosing the number of computers to operate OracleAS Web Cache, as well as defining separate hardware profile for OracleAS Web Cache servers and J2EE or OracleAS Portal servers. Typically, a large amount of RAM and fast access to file storage are the most critical components in the performance of the OracleAS Web Cache server. Another possibility is to place a firewall between OracleAS Web Cache and the Oracle HTTP Server; this would provide an additional layer of security.
|
Note: In an OracleAS Portal environment, specific configuration is needed to ensure that cache invalidation messages can reach, and be correctly routed to, the Web Server Tier. |
For additional information on configuration variants with OracleAS Web Cache, see the Oracle Application Server Web Cache Administrator's Guide.
The architectures described in this guide can be deployed in environments with additional forward or reverse proxy servers.Proxy scenarios change the way the clients' IP addresses are seen by the Oracle HTTP Server. This can be adjusted to better match Web applications' expectations by transferring the clients' IP addresses through proxies in additional HTTP headers and making the HTTP Server use the header values, either with explicit configuration or implicitly, by overall replacing the "physical" request connection information with the header values.The Oracle HTTP Server and applications in an Oracle HTTP Server handle information about clients. Because clients are often identified by their IP addresses, scenarios in which reverse ("transparent") or forward ("normal") proxies are part of the whole system may require adjustments in how the client's IP addresses are seen by the Oracle HTTP Server.For instructions on how to configure a reverse proxy using Oracle HTTP Server or the Internet Information Services (IIS) server, see Section 9.2, "Configuring a Reverse Proxy for OracleAS Portal and OracleAS Single Sign-On". For information on how to integrate OracleAS Web Cache with an additional proxy server, see the Oracle Application Server Web Cache Administrator's Guide.
There are two ways to install Oracle HTTP Server on the Web Server Tier: as a standalone Web server, or as part of the J2EE and Web Cache installation type.
Some security plans discourage installation of any Java executables on the Web Server tier. For this reason, this guide presents the installation of the Oracle HTTP Server as a standalone Web server. The Oracle HTTP Server is managed by the opmnctl utility (invoked by the Start menu on Windows systems) instead of the Oracle Enterprise Manager 10g Application Server Control Console.
If it is acceptable or desirable to install all of the J2EE and Web Cache components on the Web Server tier, or you want to use the Oracle Enterprise Manager 10g Application Server Control Console to manage the Oracle HTTP Server, you may follow the instructions in Section 9.3, "Configuring J2EE and Web Cache on the Web Tier".
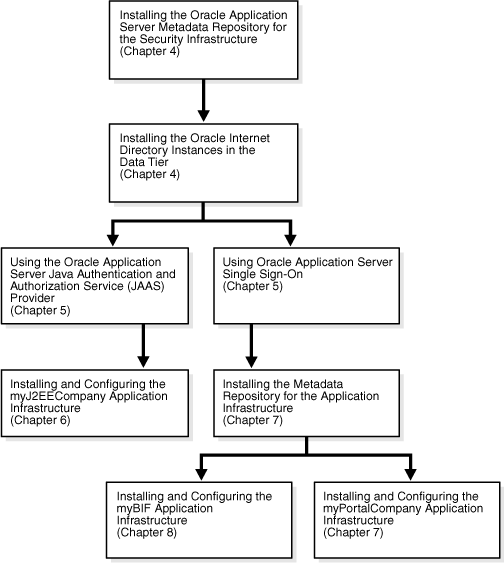
The configuration process for each architecture is detailed in the following sections.You will select chapters from this guide to install and configure a given architecture. Figure 2-4 depicts this progression of tasks and chapters.
Figure 2-4 The Enterprise Deployment Configuration Process
Install the Metadata Repository on INFRADBHOST1 and INFRADBHOST2, as described in Section 4.1, "Installing the Oracle Application Server Metadata Repository for the Security Infrastructure".
Install Oracle Internet Directory on OIDHOST1 and OIDHOST2, as described in Section 4.2, "Installing the Oracle Internet Directory Instances in the Data Tier".
Configure the Load Balancing Router or proxy server and related components, as described in Section 6.2, "Configuring the Load Balancing Router or Proxy Server".
Install an Oracle Application Server J2EE and Web Cache instance on APPHOST1 and APPHOST2, as described in Section 6.3.1, "Installing the First Application Tier Application Server Instance on APPHOST1" and Section 6.3.2, "Installing the Second Application Tier Application Server Instance on APPHOST2".
Create OC4J instances in the Oracle Application Server instance on APPHOST1, as described in Section 6.3.3, "Creating OC4J Instances on the Application Tier".
Deploy applications on APPHOST1, as described in Section 6.3.4, "Deploying J2EE Applications".
Create a DCM-Managed Oracle Application Server Cluster and add the instances to it, as described in Section 6.3.5, "Creating a DCM-Managed Oracle Application Server Cluster on the Application Tier".
Install a standalone Oracle Application Server J2EE and Web Cache instance on WEBHOST1 and WEBHOST2, as described in Section 6.4.1, "Installing the Oracle HTTP Servers on WEBHOST1 and WEBHOST2".
Configure the Manually Managed Oracle Application Server Cluster as described in Section 6.5, "Configuring the Manually Managed Oracle Application Server Cluster".
Configure the Load Balancing Router as described inSection 6.2, "Configuring the Load Balancing Router or Proxy Server".
Configure the Oracle HTTP Server with the Load Balancing Router as described in Section 6.6, "Configuring the Oracle HTTP Server with the Load Balancing Router".
Configure OC4J routing as described in Section 6.7, "Configuring OC4J Routing".
Configure application authentication and authorization with the Oracle Application Server Java Authentication and Authorization Service (JAAS) Provider as described in Section 5.2, "Option 2: Using the Oracle Application Server Java Authentication and Authorization Service (JAAS) Provider".
Install the Metadata Repository on INFRADBHOST1 and INFRADBHOST2, as described in Section 4.1, "Installing the Oracle Application Server Metadata Repository for the Security Infrastructure".
Configure the Load Balancing Router or proxy server, as described in Section 7.2, "Configuring the Load Balancing Router or Proxy Server".
Install Oracle Internet Directory on OIDHOST1 and OIDHOST2, as described in Section 4.2, "Installing the Oracle Internet Directory Instances in the Data Tier".
Install Oracle Delegated Administration Services, Oracle Application Server Single Sign-On and Oracle HTTP Server on IDMHOST1 and IDMHOST2, as described in Section 5.1.1, "Installing the First Identity Management Configuration" and Section 5.1.3, "Installing the Second Identity Management Configuration".
Install OracleAS Web Cache, OracleAS Portal, and Oracle HTTP Server on APPHOST1, as described in Section 7.3.1, "Installing the First Application Server on APPHOST1".
Configure application server components on APPHOST1, as described in Section 7.3.3, "Configuring the First Application Server on APPHOST1".
Configure the Load Balancing Router or proxy server and related components, as described in Section 7.2, "Configuring the Load Balancing Router or Proxy Server".
Install OracleAS Web Cache, OracleAS Portal, and Oracle HTTP Server on APPHOST2, as described in Section 7.3.4, "Installing the Second Application Server on APPHOST2".
Configure application server components on APPHOST2, as described in Section 7.3.5, "Configuring the Second Application Server on APPHOST2".
Complete the system configuration, as described in:
Section 7.3.6, "Configuring OracleAS Web Cache Clusters"
Section 7.3.7, "Configuring Load Balancing and Monitoring"
Section 7.3.8, "Enabling Session Binding on OracleAS Web Cache Clusters"
Section 7.3.9, "Modifying the Oracle Application Server Welcome Page"
Test the configuration, as described in Section 7.4, "Testing the Application Server Tier".
If applicable, configure custom providers as described in Section 7.5, "Configuring Custom Java Portal Development Kit (JPDK) Providers".
Install the Metadata Repository on INFRADBHOST1 and INFRADBHOST2, as described in Section 4.1, "Installing the Oracle Application Server Metadata Repository for the Security Infrastructure".
Configure the Load Balancing Router or proxy server, as described in Section 7.2, "Configuring the Load Balancing Router or Proxy Server".
Install Oracle Internet Directory on OIDHOST1 and OIDHOST2, as described in Section 4.2, "Installing the Oracle Internet Directory Instances in the Data Tier".
Install Oracle Delegated Administration Services, Oracle Application Server Single Sign-On and Oracle HTTP Server on IDMHOST1 and IDMHOST2, as described in Section 5.1.1, "Installing the First Identity Management Configuration" and Section 5.1.3, "Installing the Second Identity Management Configuration".
Install Oracle Application Server 10g Portal, Oracle Application Server 10g Discoverer, Oracle Application Server 10g Reports Services, and Oracle Application Server 10g Forms Services on APPHOST1, as described in Section 8.3.1, "Installing the First Application Server on APPHOST1".
Configure application server components on APPHOST1, as described in Section 8.3.2, "Configuring the First Application Server on APPHOST1".
Install Oracle Application Server 10g Portal, Oracle Application Server 10g Discoverer, Oracle Application Server 10g Reports Services, and Oracle Application Server 10g Forms Services on APPHOST2, as described in Section 8.3.3, "Installing the Second Application Server on APPHOST2".
Configure application server components on APPHOST2, as described in Section 8.3.4, "Configuring the Second Application Server on APPHOST2".
Table 2-15 summarizes the configurations in terms of deployed components, the number of physical servers and tiers used, and the estimated duration of installation and configuration activities.
Table 2-15 Deployment Architecture Selection Data
| Installation Type/Components | Identity Management Components | myJ2EE | myPortal | MyBIF |
|---|---|---|---|---|
|
Deployed components |
OHS SSO / DAS OID |
Web Cache OHS OC4J |
Web Cache OHS Portal |
Web Cache OHS OC4J Discoverer Forms |
|
Number of servers (without database servers) |
4 |
6 |
6 |
6 |
|
Number of server tiers |
3 |
4 |
3 |
3 or 4 |
|
Average time to install and configure |
5 hours |
5 hours |
10 hours |
4 hours |