|
Oracle® Application Server Security Guide
10g Release 2 (10.1.2) B13999-03 |
|
 Previous |
 Next |
|
Oracle® Application Server Security Guide
10g Release 2 (10.1.2) B13999-03 |
|
 Previous |
 Next |
This chapter provides an overview of the security architecture of Oracle Application Server in the following topics:
Oracle Application Server provides a solid framework for building and deploying Web applications using the Apache-based Oracle HTTP Server, Oracle Application Server Containers for J2EE, and OracleAS Portal, which use the advanced security functionality provided by Oracle Application Server Infrastructure. Oracle Application Server Infrastructure consists of Oracle Application Server Metadata Repository and Oracle Identity Management. Oracle Application Server security starts from the well-tested and highly configurable Web security services provided by Oracle HTTP Server, adds a comprehensive set of Web single sign-on services, and extends them further with centralized user provisioning that is available in Oracle Internet Directory, an LDAP, version 3-compliant directory service. In addition, Oracle Application Server provides the Oracle implementation of Java Authentication and Authorization Services (JAAS) for J2EE application security, and extensive portal authorization and application integration mechanisms. Oracle Application Server also supports secure access to Oracle database systems using Oracle Advanced Security.
Figure 2-1 illustrates the flow of information among the elements of Oracle Application Server.
Figure 2-1 Components of Oracle Application Server
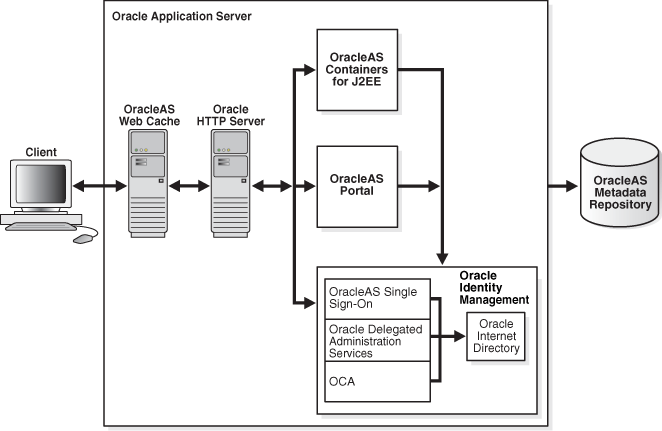
The remainder of this chapter discusses each element in greater detail.
The Oracle HTTP Server provides the first line of defense in Oracle Application Server security. The Oracle HTTP Server makes data available to users through a standard Web interface. Oracle HTTP Server mediates user access to both static and dynamic content by restricting access to URLs and directories on the server. Dynamic content is provided by applications running natively on Oracle HTTP Server, such as CGI, or in other Oracle Application Server components. These components include J2EE applications deployed on Oracle Application Server Containers for J2EE (OC4J) and accessed through mod_oc4j, as well as PL/SQL applications deployed on an Oracle Database and accessed through mod_plsql. You configure access to resources on Oracle HTTP Server using the standard Apache directive model; see the Oracle HTTP Server Administrator's Guide for details.
The Oracle HTTP Server controls access to resources based on user identity. Identity is established through standard Apache authentication mechanisms, such as basic authentication and SSL with client certificate. Users can also be authenticated through OracleAS Single Sign-On, using mod_osso; this is described in detail in the Oracle Identity Management Concepts and Deployment Planning Guide. Applications running on Oracle Application Server can obtain OracleAS Single Sign-On user identity from Oracle HTTP Server using the Apache header created by mod_osso.
In Oracle Application Server 10g, when users are authenticated by mod_osso, control of user access on Oracle HTTP Server is limited to specifying whether a user may have access to server resources (URLs, directories) or not. Applications accessible through Oracle HTTP Server can use the SSO-authenticated user identity to enforce fine-grained control of user access to resources that are managed by those applications. The Oracle HTTP Server does not itself provide fine-grained access control of users to static content on the HTTP Server when users are authenticated using SSO.
|
Note: If you protect your J2EE applications with OracleAS Single Sign-On, there is no need to configuremod_osso separately.
|
Oracle HTTP Server can be configured to protect data exchanged between the server and Web clients using the Secure Sockets Layer (SSL) cryptographic protocol. The SSL protocol is an industry-accepted standard for network transport layer security. SSL provides encryption and data integrity, and support for digital certificate authentication using a public key infrastructure (PKI). Digital certificates for SSL authentication require use of an Oracle Wallet; for more information, see the Oracle Application Server Administrator's Guide.
Figure 2-2 shows the flow of information when a user requests the URL for a partner application using the Oracle HTTP authentication module mod_osso.
The user tries to access a partner application.
The user is redirected to the single sign-on server. The server challenges her for her credentials. After verifying these credentials in Oracle Internet Directory, it passes them on to the partner application
The application serves up the requested content.
OracleAS Single Sign-On uses the following process if the user is accessing an external application for the first time.
The external application login procedure checks the single sign-on server password store for the user's credentials for the requested external application. If it finds that the user has no such credentials, the single sign-on server prompts the user for them.
The user enters the user name and password.
If the user elects to save the credentials in the single sign-on server password store, the server uses these credentials to construct a login form to submit to the login processing routine for the external application. This routine has been preconfigured by the single sign-on server administrator and is associated with the requested application.
The single sign-on server sends the form to the client browser, with a directive to post it immediately to the external application.
The client posts the form to the external application and logs the user in.
If the user declines to save her credentials in the single sign-on password store, she must enter a user name and password each time she logs in to the application.
In addition to offboard SSL acceleration solutions, Oracle Application Server now supports BHAPI-compliant hardware for deployment on servers running Oracle Application Server Web Cache and/or Oracle HTTP Server. When executed in software, SSL operations place a strain on server CPU resources, causing a reduction in throughput and slower overall performance. The hardware offloads the SSL key exchange processing from a server's CPUs, increasing the number of concurrent SSL connections and improving response times for SSL-protected content.
J2EE is the primary application development and deployment environment supported by Oracle Application Server. Oracle provides Oracle Application Server Java Authentication and Authorization Service (JAAS) Provider to authenticate users and manage their access privileges.
The OracleAS JAAS Provider allows user authentication and authorization information to be managed in two ways. For Oracle Application Server Java Edition deployments that do not use Oracle Identity Management, user information can be managed in a flat file in XML format. For Oracle Application Server deployments in which Oracle Identity Management is installed, the OracleAS JAAS Provider can also leverage Oracle Identity Management. In this case, user authentication and authorization information is managed in Oracle Internet Directory, and the OracleAS JAAS Provider can leverage Oracle Application Server Single Sign-On for user authentication. In this case, users can be provisioned using the Oracle Delegated Administration Services component of Oracle Identity Management, or can be managed in and provisioned from a third-party repository using the Directory Integration and Provisioning component. Directory Integration and Provisioning specifically allows OracleAS JAAS Provider user information to be managed in a third-party LDAP directory, using a connector to Oracle Internet Directory.
A major benefit of using the OracleAS JAAS Provider with Oracle Identity Management is that any J2EE applications deployed on Oracle Application Server, whether developed by Oracle, a customer, or a third party, can share a common framework for user authentication and authorization. This framework is integrated with every component of Oracle Application Server, as well as with other Oracle products, such as the Oracle Database, Oracle Collaboration Suite, and Oracle E-Business Suite. Another benefit of using Oracle Identity Management is that it can scale to support millions of users, and manages their information in a reliable, highly available, and secure directory. For more information on Oracle Internet Directory, Oracle Application Server Single Sign-On, and other components of Oracle Identity Management, see the Oracle Identity Management Concepts and Deployment Planning Guide
Oracle Application Server 10g fully integrates JAAS with the J2EE security model, allowing customers to deploy custom JAAS LoginModules. These can be used to authenticate users with third-party authentication mechanisms, or to manage JAAS user information in third-party directories when Oracle Identity Management has not been installed (for example, in Oracle Application Server Java Edition).
Another feature of Oracle Application Server 10g is that the Apache Java Protocol (AJP) can now be used with SSL encryption. AJP is used when Oracle HTTP Server and OC4J are deployed on physically separate servers. SSL protection of AJP ensures that any sensitive data exchanged between Oracle HTTP Server and OC4J is protected against disclosure or modification in the communication network.
OracleAS Portal allows customers to organize Web content and applications in a logical and consistent Web portal format. OracleAS Portal provides a flexible, sophisticated model for managing user access to OracleAS Portal resources based on user identity and privilege. It supports a hierarchical, group-based model for aggregating privileges. A collection of privileges is associated with each group, and users who are members of that group inherit the appropriate privileges. The model is hierarchical: groups may be defined as subgroups of other groups. In this case, users who belong to the subgroup inherit all the privileges of the larger group in addition to privileges unique to the subgroup.
As do other components of Oracle Application Server, OracleAS Portal uses Oracle Identity Management for user management, authentication, and authorization. After users have been provisioned in the Oracle Internet Directory component of Oracle Identity Management, they can authenticate themselves to OracleAS Portal using Oracle Application Server Single Sign-On.
OracleAS Web Cache serves as a caching front end to Oracle HTTP Server. When used, it intercepts HTTP requests sent to Oracle HTTP Server, and proxies them to Oracle HTTP Server if necessary. Because it acts as a proxy, OracleAS Web Cache necessarily terminates any SSL connections established by a client system to Oracle Application Server. If the SSL connection uses client certificate authentication, then the client certificate identity is provided to OracleAS Web Cache, and not to Oracle HTTP Server, because the SSL connection is established between the client and OracleAS Web Cache.
OracleAS Web Cache can proxy the contents of a client certificate, when used in an SSL connection, to Oracle HTTP Server. In this way, a client's SSL authenticated identity can be obtained and used by Oracle HTTP Server, even if OracleAS Web Cache is used in front of Oracle HTTP Server.
Oracle Application Server supports Oracle products for data reporting (OracleAS Forms Services, OracleAS Reports Services), business intelligence (OracleBI Discoverer), and other purposes. These applications may have application-specific privileges and data security models, but all of them leverage Oracle Identity Management for user management, authentication, and authorization. For more information on security associated with these products, please refer to the security sections in the individual product documentation.
When Oracle Application Server accesses an Oracle database, customers may wish to protect data exchanged between Oracle Application Server and the database using a cryptographically protected network protocol. Network encryption is one of the features offered in the Oracle Advanced Security option available with the Oracle Database. Please refer to the Oracle Advanced Security Administrator's Guide for the available algorithms and configuration details.