|
Oracle® Application Server High Availability Guide
10g Release 2 (10.1.2) B14003-03 |
|
 Previous |
 Next |
|
Oracle® Application Server High Availability Guide
10g Release 2 (10.1.2) B14003-03 |
|
 Previous |
 Next |
This chapter provides an overview of transforming non-highly available OracleAS Infrastructure topologies to highly available topologies.
The chapters in this section describe transformation for OracleAS Infrastructure only. Typically, you configure OracleAS Infrastructure for high availability during installation. If you installed OracleAS Infrastructure without high availability configuration, you can use the transformation procedures to transform the non-highly available OracleAS Infrastructure to highly available after installation.
Transformation does not apply to middle tiers because, unlike OracleAS Infrastructure, you do not configure high availability for middle tiers during installation. To make middle tiers highly available, you configure them after installation. See the chapters in Part II, "Middle-tier High Availability", for details.
Sections in this chapter:
Although Oracle Application Server supports many different configurations, the transformation procedures are designed for a non-highly available configuration (the source configuration) that consists of:
OracleAS Metadata Repository installed through OracleAS Metadata Repository Creation Assistant in an existing single-instance database. The version of the database is either Oracle9i Release 2 (9.2.0.6) or Oracle Database 10g Release 1 (10.1.0.4).
Oracle Identity Management is installed in its own Oracle home.
The source configuration is always the same, regardless of which target configuration you select.
You can transform the source configuration into any of the high availability configurations shown in Table 19-1.
During the transformation process, you transform the OracleAS Metadata Repository and the Oracle Identity Management components. Table 19-1 shows what these components are transformed to. The database and Oracle Application Server versions are not changed.
Note that you may need additional hardware (such as additional nodes or load balancers) and software (such as vendor clusterware) to create the high availability configuration.
Table 19-1 Transformation Targets
| Target Configuration | OracleAS Metadata Repository
|
Oracle Identity Management
|
|---|---|---|
|
OracleAS Cluster (Identity Management) |
Transformed to a Real Application Clusters database. You need a hardware cluster with at least two nodes for the Real Application Clusters database. |
Transformed to OracleAS Cluster (Identity Management). You need to install one additional instance of Oracle Identity Management on a new node. You also need a load balancer in front of the nodes running Oracle Identity Management instances. |
|
Distributed OracleAS Cluster (Identity Management) |
Transformed to a Real Application Clusters database. You need a hardware cluster with at least two nodes for the Real Application Clusters database. |
Transformed to a distributed OracleAS Cluster (Identity Management). In this environment, you run OracleAS Single Sign-On / Oracle Delegated Administration Services on one set of nodes, and Oracle Internet Directory / Oracle Directory Integration and Provisioning on another set of nodes. You need additional nodes to run the additional instances of OracleAS Single Sign-On / Oracle Delegated Administration Services and Oracle Internet Directory / Oracle Directory Integration and Provisioning. |
|
OracleAS Cold Failover Cluster (Identity Management) |
Transformed to a cold failover cluster database. To create a cold failover cluster database, you need nodes that are in a hardware cluster and a virtual hostname and IP for the hardware cluster. |
Transformed to OracleAS Cold Failover Cluster (Identity Management). To create OracleAS Cold Failover Cluster (Identity Management), you need nodes in a hardware cluster and a virtual hostname and IP for the hardware cluster. |
|
Distributed OracleAS Cold Failover Cluster (Identity Management) |
Transformed to a cold failover cluster database. To create a cold failover cluster database, you need nodes that are in a hardware cluster and a virtual hostname and IP for the hardware cluster. |
Transformed to a distributed OracleAS Cold Failover Cluster (Identity Management). In this environment, you run Oracle Internet Directory / Oracle Directory Integration and Provisioning on nodes in a hardware cluster. This results in an active-passive configuration. You need a virtual hostname and IP for the hardware cluster. For OracleAS Single Sign-On / Oracle Delegated Administration Services, you run them on a different set of nodes in an OracleAS Cluster (Identity Management) topology. The results in an active-active configuration, and you need a load balancer in front of these nodes. |
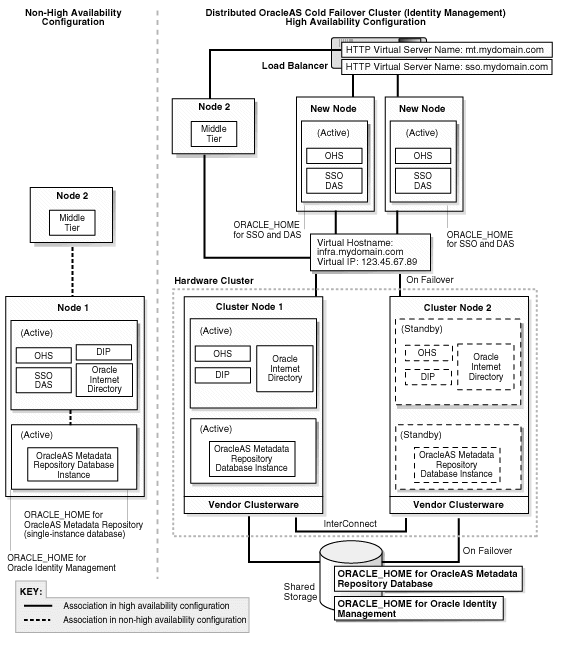
Figure 19-1 shows the transformation to OracleAS Cluster (Identity Management). For this transformation, you transform the single-instance OracleAS Metadata Repository database to a Real Application Clusters database, and the Oracle Identity Management to OracleAS Cluster (Identity Management).
This results in an active-active topology. For details on this topology, see Section 9.6, "OracleAS Cluster (Identity Management) Topology".
You need a hardware cluster with two or more nodes for the Real Application Clusters database, and additional nodes for the OracleAS Cluster (Identity Management). You also need a load balancer in front of the nodes for the OracleAS Cluster (Identity Management).
For details on this transformation, see Chapter 20, "Transforming to OracleAS Cluster (Identity Management) Topologies".
Figure 19-1 Transforming to OracleAS Cluster (Identity Management)
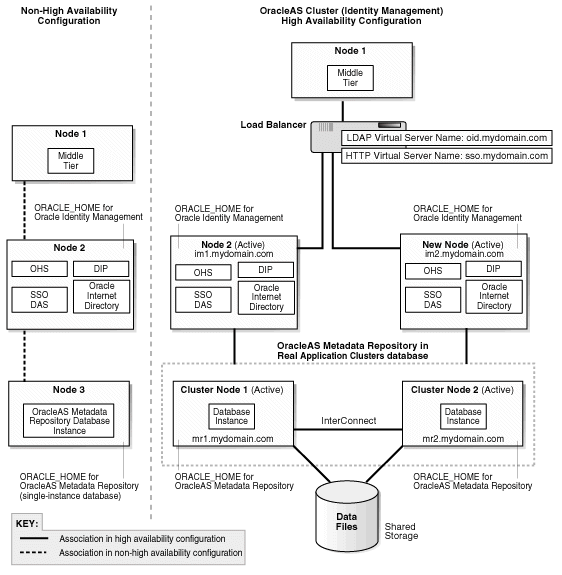
This is similar to transforming to OracleAS Cluster (Identity Management), except that you run OracleAS Single Sign-On and Oracle Delegated Administration Services on one set of nodes, and Oracle Internet Directory and Oracle Directory Integration and Provisioning on another set of nodes. Figure 19-2 shows this transformation.
For details on a distributed OracleAS Cluster (Identity Management) topology, see Section 9.7, "DistributedOracleAS Cluster (Identity Management) Topology".
For details on this transformation, see Chapter 20, "Transforming to OracleAS Cluster (Identity Management) Topologies".
Figure 19-2 Transforming to Distributed OracleAS Cluster (Identity Management)
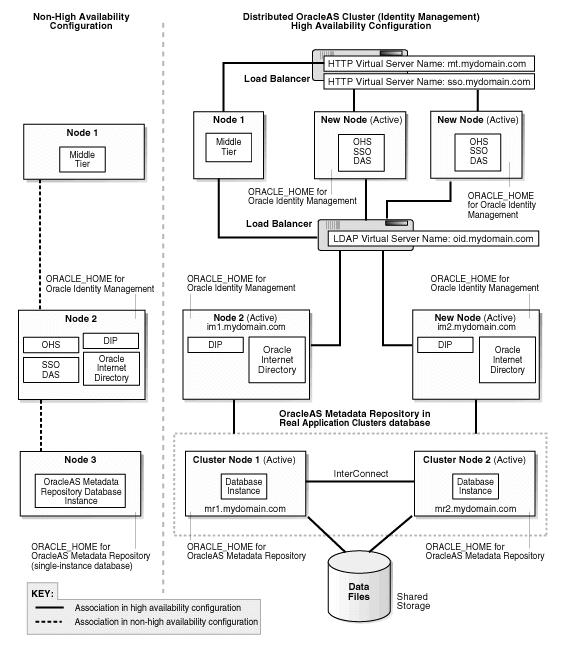
In this transformation (Figure 19-3), you transform the database to a cold failover cluster database, and the Oracle Identity Management to OracleAS Cold Failover Cluster (Identity Management).
This results in an active-passive topology. In this topology, you have two nodes in a hardware cluster, where only one node is active at any given time. The passive node becomes active when the currently active node fails. For details on this topology, see Section 9.4, "OracleAS Cold Failover Cluster (Identity Management) Topology". For details on cold failover databases, see Section 7.1, "Cold Failover Cluster Databases".
The nodes in the hardware cluster have access to a shared storage.
If you are running on UNIX platforms, on the shared storage, you install the Oracle homes for the database and for Oracle Identity Management (see Figure 19-3).
If you are running on Windows, you install the Oracle home for the database on the local storage of each node, not on the shared storage, but you place the data files on the shared storage (see Figure 21-7).
For details on this transformation, see Chapter 21, "Transforming to OracleAS Cold Failover Cluster Topologies".
Figure 19-3 Transforming to OracleAS Cold Failover Cluster (Identity Management) on UNIX
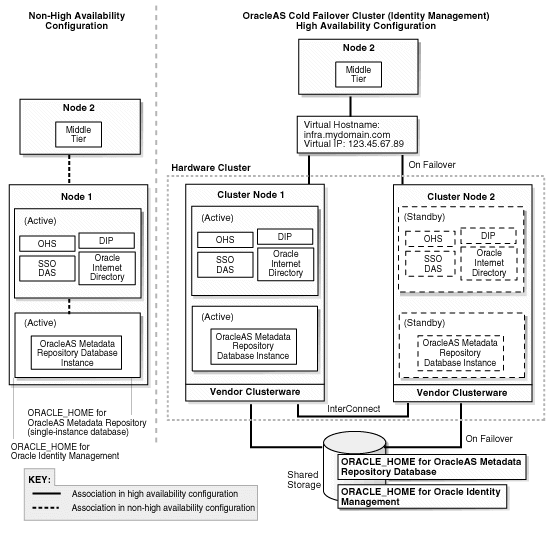
This transformation (see Figure 19-4) is similar to transforming to OracleAS Cold Failover Cluster (Identity Management), except that the OracleAS Single Sign-On and Oracle Delegated Administration Services components run in an active-active configuration.
You transform the OracleAS Metadata Repository to a cold failover cluster database. This is an active-passive configuration. To run a cold failover cluster database, you need two nodes in a hardware cluster, where only one node is active at any time. If the active node fails, the other node becomes the active node.
You need a virtual hostname and IP for this hardware cluster.
On UNIX, you install the Oracle home for the database and the data files on the shared storage. Figure 19-4 shows the UNIX version of the transformation.
On Windows, you install the Oracle home for the database on the local storage of each node, but you place the data files on the shared storage.
For the Oracle Identity Management components:
You transform Oracle Internet Directory and Oracle Directory Integration and Provisioning to a distributed OracleAS Cold Failover Cluster (Identity Management). This is an active-passive configuration.
You also need a two-node hardware cluster for this active-passive configuration, and a virtual hostname and IP for the hardware cluster. You can use the same hardware cluster that you are using for the cold failover cluster database, or you can use a different hardware cluster.
You install new instances of OracleAS Single Sign-On and Oracle Delegated Administration Services on their own set of nodes. You configure these components in an OracleAS Cluster (Identity Management). This results in an active-active configuration. You need a load balancer in front of these nodes.
For details on the Distributed OracleAS Cold Failover Cluster (Identity Management) topology, see Section 9.5, "DistributedOracleAS Cold Failover Cluster (Identity Management) Topology".
For details on this transformation, see Chapter 21, "Transforming to OracleAS Cold Failover Cluster Topologies".
Figure 19-4 Transforming to Distributed OracleAS Cold Failover Cluster (Identity Management) on UNIX