|
Oracle® Application Server Certificate Authority Administrator's Guide
10g Release 2 (10.1.2) B14080-02 |
|
 Previous |
 Next |
|
Oracle® Application Server Certificate Authority Administrator's Guide
10g Release 2 (10.1.2) B14080-02 |
|
 Previous |
 Next |
The Oracle Application Server Certificate Authority web administrative interface covers the following three broad areas, each accessible from a tab on the home page:
Managing certificate issues: requests for certificate issuance, revocation, or renewal; certificates already issued; and certificate revocation lists (CRLs)
Managing configuration issues: parameters for OracleAS Certificate Authority actions and for implementation of certificate security policies
This chapter describes the first of those three areas: certificate management. The other two are described in Chapter 5, "Configuring Oracle Application Server Certificate Authority".
Some administrative operations require the command-line interface described in Appendix A, "Command-Line Administration". Two of these operations are starting and stopping OracleAS Certificate Authority, as explained in later sections, along with requesting or replacing the administrator's certificate.
For end-user interactions with OracleAS Certificate Authority, a separate web interface presents forms enabling personal certificate-related operations: see Chapter 8, "End-User Interfaceof the Oracle Application Server Certificate Authority".
The present chapter contains the following sections:
Starting and Stopping Oracle Application Server Certificate Authority
Overview of the OracleAS Certificate Authority Administration Interface
For security reasons, OracleAS Certificate Authority's start and stop operations can only be done using the command-line tool ocactl, which requires the administrator's password. An example of using these operations appears in Replacing the Administrator Certificate. This tool is fully described in Appendix A, "Command-Line Administration".
Before OracleAS Certificate Authority can be started, the following five components must be operating or available:
and optionally OracleAS Single Sign-On
If OracleAS Certificate Authority is installed in a different $ORACLE_HOME from the other infrastructure components, then OHS and OracleAS Certificate Authority's OC4J must be started separately, after the repository. Use this command in OracleAS Certificate Authority's $ORACLE_HOME:
$ORACLE_HOME/opmn/bin/opmnctl startall
If a single $ORACLE_HOME contains all the infrastructure components, including OracleAS Certificate Authority, then OHS and OC4J will already have been started, as in Section 4.3 earlier.
To start, stop, or restart OracleAS Certificate Authority, enter the corresponding command on the command line:
To stop OracleAS Certificate Authority, use this command:
$ORACLE_HOME/oca/bin/ocactl stop
To start OracleAS Certificate Authority, use this command:
$ORACLE_HOME/oca/bin/ocactl start
To restart OracleAS Certificate Authority, use the stop command listed in Step 1, followed by the start command listed in Step 2.
To get the status of Oracle Application Server Certificate Authority, use this command:
$ORACLE_HOME/oca/bin/ocactl status
You must have the administrator certificate before you can use any of the Oracle Application Server Certificate Authority administrative options and controls in the web interface. If you have the administrator password created during installation, this certificate is easy to get, and is the first step you must do before any other task.
In other systems, requesting, acquiring, and installing your administrator PKI certificate required a whole set of command-line, floppy disk, and cut-and-paste operations.
With OracleAS Certificate Authority, however, the process is simple and easy:
To request the administrator certificate for your authentication, you simply fill in and submit a brief form that appears after OracleAS Certificate Authority is started for the first time. You must be accessing OracleAS Certificate Authority from the computer you intend to use as the administrator. Clicking the Certificate Management tab displays a Welcome page, followed by a form requesting your identifying data.
The form requires your common name, organization, and the OracleAS Certificate Authority administrator password created during installation. You can also supply other DN information: your email address, organizational unit, locality, state, and country.
You can select the certificate key size (default: 2048) and the validity period (default: 1 year).
When the administrator certificate is issued, you install it into your browser. With this certificate in your browser, you can access the OracleAS Certificate Authority facilities in the administration and configuration interfaces to manage certificate requests, certificate revocation or renewal, and policies.
This simple process — easy installation after filling in a simple request-form — replaces all the operations formerly required (before OracleAS Certificate Authority) for PKI certificate acquisition and use.
To request your certificate, perform the following steps:
Access the OracleAS Certificate Authority administration interface.
Launch your web browser and enter the URL and port number of the administration server as they were displayed at the end of installation. For example:
https://Oracle_HTTP_host:ssl_port/oca/admin
where Oracle_HTTP_host is the host on which OracleAS Certificate Authority is installed, and ssl_port is listed in $ORACLE_HOME/install/portlist.ini under "Oracle Certificate Authority SSL Server Authentication port". For Windows, the path is %ORACLE_HOME\install\portlist.ini.
|
Note: If port changes have occurred since installation, then the most current information is not inportlist.ini. Instead, sign on to the Oracle Enterprise Manager Control and click the instance on which OracleAS Certificate Authority was installed. Then click the Ports link, find the entry in the Type column that says "OracleAS Certificate Authority Server Authentication (SSL)", and use the number in the adjacent column, headed "Port In Use".
|
The screen displays a welcome page. Clicking the link provided there displays the form to request the administrator certificate.
Enter into that form the DN, password, and certificate information to request your certificate:
DN Information: Enter the data for the distinguished name (DN) that will identify the administrator as the certified owner of the certificate.
Table 4-1 DN Information for the Administrator's Certificate
Certificate Authority Administrator Password: Only the OracleAS Certificate Authority administrator can do certificate and configuration management. This person is initially authenticated by entering here the password as entered during OracleAS Certificate Authority installation, in the screen named "Specify OCA Administrator Password".
Passwords must
Begin with an alphabetic character from your database character set
Be at least eight characters long
Contain at least one alphabetic character and at least one non-alphabetic character, that is, a numeric or special character
Use only characters in the ASCII character set
Be different from all Oracle reserved words; and
Contain only alphanumeric characters from your database character set. If needed, the underscore (_), dollar sign ($), or pound sign (#) can also be used, although Oracle Corporation strongly discourages you from using the characters $ and #.
Thus during installation, the password you choose for the OracleAS Certificate Authority administrator must accommodate these restrictions.
If your database will be using Oracle's password complexity verification routine (specified using the PL/SQL script UTLPWDMG.SQL), then the password must also meet the following requirements (or additional requirements that you add to that script):
Be at least four characters long
Differ from the username
Have at least one alpha, one numeric, and one punctuation mark character
Be different from simple or obvious words, such as welcome, account, database, or user
Subsequent changes to this password must also differ from the previous password by at least 3 characters.
Certificate Information: The two vital data for creating a new certificate are the size of its keys and the period of its validity (or its expiration date). In this section of the form, you choose these parameters.
In Netscape, the phrase Certificate Key Size appears, referring to the size in bits of the key-pair to be generated: 512-bit, 1024-bit, or 2048-bit. Choose the size appropriate to your site: 2048-bit is OracleAS Certificate Authority's default, providing excellent security. Higher numbers improve the security at some price in performance.
In Internet Explorer, the phrase Cryptographic Service Provider appears, referring to a choice of providers for cryptography service. Standard choices include key sizes of 512-bit (Microsoft Basic Crypto Provider), 1024-bit (Microsoft Enhanced Crypto Provider), and 2048-bit (Microsoft Strong Cryptographic Provider). OracleAS Certificate Authority's default is the "Strong" choice, if available, followed by Enhanced, if available, and then by Basic. Other choices may also be present, such as Gemplus for smartcard usage. Select the size according to your requirements.
This section of the form will look like this:
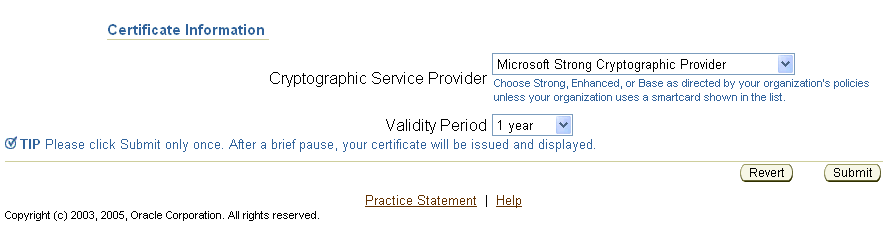
OracleAS Certificate Authority recommends using Microsoft Strong Cryptographic Provider for the Administrator Certificate. However, if readers for smartcards like Gemplus or Schlumberger are available, they should be used; if no reader is installed, selecting smartcard suppliers causes an error.
Validity Period: The duration of the certificate's validity. The standard default of 1 year is shown, but you can choose your desired period.
If you need to start over, click the Reset button.
To send your request for the Administrator certificate, click Submit. (You may have to supply your browser security password.)
Follow the instructions that your browser presents as it generates a key-pair. This process can take a few minutes, depending on keysize chosen and processor/memory limitations.
Click Install in Browser. (You may have to supply your browser security password.)
Now you have a client authentication certificate in the common name you specified.
At this point, you can perform any of the tasks available through the web interface of OracleAS Certificate Authority, as described in Chapter 5, "Configuring Oracle Application Server Certificate Authority".
Click Administration Home to access the welcome page for OracleAS Certificate Authority.
You may in future need to replace the administrator's certificate. Reasons could include the password to your private key being lost, the private key somehow being compromised or stolen, or the administrator role being given to someone new.
To replace the administrator certificate, you must stop the server, revoke the current administrator's certificate, and restart the server. These tasks are performed by using the command-line tool ocactl, which requires the OracleAS Certificate Authority Administrator password. For security reasons, these commands are only enabled on the command line and not through the graphical user interface (GUI).
The administrator then navigates to the Oracle Application Server Certificate Authority web page and fills in the form presented for Web Administrator Enrollment, as described earlier in "Requesting the Administrator Certificate".
Here are the three relevant command-line tasks:
To stop the OracleAS Certificate Authority server, enter the following command on the command line:
$ORACLE_HOME/oca/bin/ocactl stop
To revoke the administrator's certificate, enter the following command:
$ORACLE_HOME/oca/bin/ocactl revokecert -type WEBADMIN -reason REASON_CODE
Note: You may choose any one of the following reason codes (separated by | ):
{KEY_COMPROMISE | CA_COMPROMISE | AFFILIATION_CHANGE | SUPERSEDED | CESSATION_OF_OPERATION | CERTIFICATE_HOLD | REMOVE_FROM_CRL | UNSPECIFIED}
You may want to change the administrative password as well. See "Changing Privileged Passwords" in Appendix A, "Command-Line Administration".
On the command line, start OracleAS Certificate Authority services by entering one of the following commands:
For UNIX, enter $ORACLE_HOME/oca/bin/ocactl start
For Windows, enter %ORACLE_HOME%\oca\bin\ocactl start.
At this point, follow the instructions at "Requesting the Administrator Certificate" to obtain that certificate, enabling all administrative capabilities.
To perform administrative tasks you must have a valid administrator certificate. If your initial sign-in is as a regular user, rather than as administrator, you may get the error message described in Appendix C, "Troubleshooting OracleAS Certificate Authority", in section "Prerequisite Issues and Warnings", item "Key Pair Generation Fails during Certificate Requests on Windows"
To access the OracleAS Certificate Authority administration interface, launch your web browser. Enter the URL and port number of the administration server as they were displayed at the end of installation:
https://Oracle_HTTP_host:ssl_port/oca/admin
For information about the host and port number in the URL, see "Requesting the Administrator Certificate", Step 1.
After issuing the command to start OracleAS Certificate Authority, the OracleAS Certificate Authority home page appears, presenting three additional subtabs, as the following figure shows:
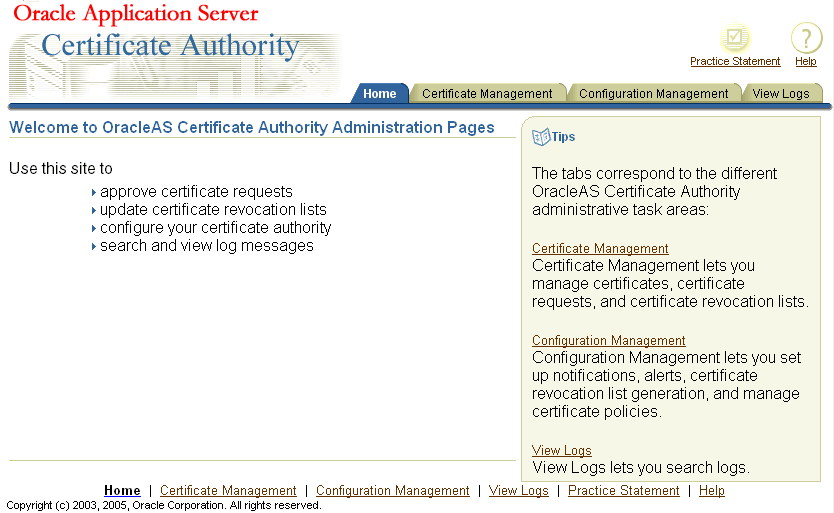
These three subtabs enable you to address specific tasks in managing certificates or the Certificate Authority configuration:
"Certificate Management Tab", described in this chapter
"Configuration Management Tab", described in Chapter 5, "Configuring Oracle Application Server Certificate Authority"
"View Logs Tab", described in Chapter 5
The Certificate Management tab shows all the pending certificate requests, displaying a page that looks like the following:
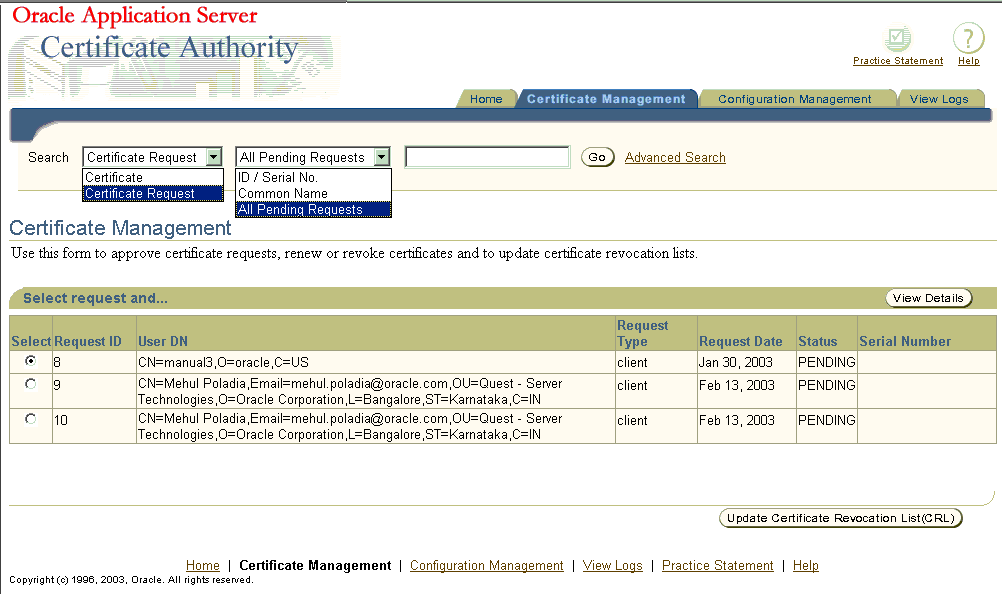
This page enables the administrator to choose among the following tasks:
Oracle Application Server Certificate Authority maintains a master list of all certificate requests and their current status: pending, rejected, or certified. Upon entering the Certificate Management tab, all certificate requests needing action (pending) are displayed. The administrator is responsible for approving or rejecting such requests, for revoking or renewing certificates as needed, and for managing the Certificate Revocation List (CRL) generation.
In performing these tasks as the administrator, you can search the master lists of certificates or certificate requests by name or number, and then examine specific certificates or requests of interest.
You can then
revoke specific issued certificates, if they have been compromised or are no longer appropriate, such as being owned by someone who has left the company, or renew any existing certificate during a brief period just before or after it expires.
|
See Also: You can specify this renewal-period window: see Chapter 6, "Managing Policies in Oracle Application Server Certificate Authority", in the following sections:
|
All of these certificate management tasks are described in the sections that follow:
The starting screen of the Certificate Management tab displays a list of all pending certificate requests. To approve or reject a certificate, follow the steps in the corresponding section.
Select the desired certificate request by clicking the radio button next to it.
Click View Details. The Certificate Request Details screen appears, displaying information about the selected certificate. The contact information of the requestor is displayed. You should follow the organization's practice of authenticating the user, such as sending him email or calling him.
For Sub CA certificate issuance, a default path length (for listing trusted certificate authorities) is displayed as 2. (You can change this if required.)
Click Approve. A message appears indicating that the certificate request is approved. Please inform the owner of the certificate request so that he can install the certificate.
Select the desired certificate request by clicking the radio button next to it. You should reject the certificate request when the requestor cannot be verified, or when the certificate properties are not correct.
Click View Details. The Certificate Request Details screen appears, displaying information about the selected certificate.
Click Reject. A message appears indicating that the selected certificate request is rejected. Please notify the requestor about the rejection.
From the Certificate Management tab, you can select a certificate and view its details.
To select a single certificate, see "Listing a Single Certificate Request or Issued Certificate".
To display a list of certificates, see "Using Advanced Search".
From your search results, select the certificate you wish to review, and click View Details. The Certificate page appears, showing the certificate's detailed contents. (This page's buttons also enable you to revoke, renew, or install the selected certificate.)
As the administrator, you can revoke certificates before their specified lifetime, and should do so if one of the following situations occurs:
The owner of the certificate has changed status and no longer has the right to use the certificate.
The private key of a certificate owner has been compromised.
For a complete list of revocation codes, see "Reasons for Revocation".
To find the target certificate, follow the instructions in "Listing a Single Certificate Request or Issued Certificate" or "Using Advanced Search" . Once you have selected the correct certificate, you can choose to review its detailed contents by clicking View Details, or revoke it with the following steps:
To submit the revocation request, click the Revoke button. The Revocation Confirmation screen will appear, where you must choose a revocation reason from these eight choices: Key Compromise, Affiliation Change, CA Compromise, Certificate Hold, Cessation of Operation, Remove From CRL, Superseded, or Unspecified.
You can then click Cancel to leave the certificate in force, or click OK to revoke it, in which case a message appears indicating that the revocation is successful.
|
See also: End-users who are using OracleAS Single Sign-On or SSL authentication can also revoke their own certificates, as described in "Certificate Revocation" in Chapter 8, "End-User Interfaceof the Oracle Application Server Certificate Authority". |
|
Notes:
|
An administrator can specify one of the following reasons when revoking a certificate:
affiliationChange: the certificate holder's relationship with the organization has been terminated
cACompromise: the private key of the certificate authority who signed the certificate has been compromised
certificateHold: the certificate has been placed on hold at this time (this amounts to a temporary revocation and it is the only reason code that allows the certificate to be assigned a different status subsequently, either to "unrevoke" the certificate for use or to revoke it with another reason code)
cessationOfOperation: the organization to whom the certificate was issued has ceased operations, and the CA's certificate is revoked using this code
keyCompromise: the private key of this certificate has been compromised
removeFromCRL: the certificate was placed on certificateHold, and is now being "unrevoked"
superseded: a new certificate has been issued in place of the existing one
unspecified: the certificate is revoked without a specific reason code; using this revocation reason is not recommended practice, however, since it makes it difficult to understand why a certificate was revoked
The administrator can renew a user certificate 10 days (default policy) before or after it expires, enabling it to continue to be used without interruption. (The administrator can alter the number of days allowed before and after expiration.) Expired certificates can be renewed during the number of days specified for the period before and after the expiration date. Once a certificate expires and is not renewed during this permitted period, it becomes unusable and must be replaced by submitting a new certificate request and having it approved.
To renew a certificate, the administrator selects it (see the sections on listing and searching), clicks View Details to display the Certificate page, and then clicks Renew. If the date is within the established window around the certificate's expiration date (default: 10 days before or after), the certificate can be renewed. Otherwise, an error message appears, regarding the established window.
For OracleAS Single Sign-On-authenticated or SSL-authenticated renewal requests, the same policy governing user certificate renewals (RenewalCertificateRequestConstraints) is applied automatically. When Oracle Application Server Certificate Authority processes renewal requests from end entities, this policy sets the new validity period for the renewed certificate.
From the first page of the user web interface, the Oracle Application Server Certificate Authority administration interface lets you display a specific certificate or certificate request. (To generate a list of certificates or requests that meet criteria you specify, see "Using Advanced Search".)
To find a specific certificate or certificate request, do the following steps:
Use the Search pull-down menus:
Fill in the Search criteria field with the value appropriate to your search request:
For All Pending Requests, no further specification is needed.
For ID/Serial, enter the serial number or the Request ID of the desired certificate or request.
For Common Name, enter the desired Common Name.
Click Go. (Pressing Enter instead of clicking Go will not work.)
A successful search for a single certificate request displays a line representing that certificate request. When you click View Details, information is displayed regarding the request, including contact, requestor, and validity period, along with buttons labeled Approve and Reject. Whichever button you click will attach the corresponding status to that request. This status will then appear with this certificate request whenever it is listed as the result of a future search.
A successful search for all pending certificate requests displays them in a list. If there are more than 25, they are displayed 25 at a time. Clicking the number identifying a request displays its details and permits you to approve or reject it.
A successful search for a single issued certificate displays a line representing that certificate, along with the View Details button. Clicking View Details shows you the data on the certificate along with buttons to Revoke, Renew, or Install in Browser. The Revoke button invalidates that certificate and tags it as Revoked in the database. At some future time, when you choose the Update CRL (Certificate Revocation List) button or when the CRL is automatically regenerated, the latest list of revoked certificates is uploaded to Oracle Internet Directory. Applications in your trust environment can use the CRL to prevent entities with revoked certificates from being authenticated.
The Advanced Search feature enables you to use more complex search criteria to find and list multiple certificates or certificate requests, as follows:
For certificate requests, separate searches can list all pending, rejected, or certified requests.
For requests or issued certificates, you can search by email address, by an advanced DN, by a serial number or range, or by specific entries in the DN, such as name, organization, state, country, and so on. These components must be presented as a contiguous string. For example, certificates owned by cn=lakshmi, ou=st, o=oracle will not be selected or found if you specify cn=lakshmi, o=oracle as the search criteria. In that specification, the search string is not contiguous because ou=st is missing.
From the results listed for a search, the administrator can select
any single certificate found in a certificate search and, after viewing its details, renew it or revoke it (or install it into the browser), or
any single request found in a certificate request search, view its details, and either approve or reject issuing a certificate.
In each type of search, after you specify your search parameters, click the Go button. OracleAS Certificate Authority displays 25 records at a time.
To perform an advanced search for certificate requests or issued certificates:
Click Advanced Search on the Certificate Management page.
The resulting page is structured in sections, each described as follows, so that you can choose the particular type of search you want, from the following choices:
Search Certificate Requests using Request Status (Pending, Rejected, or Certified)
Search Using DN (Distinguished Name) (certificates or certificate requests)
Search Using Advanced DN (certificates or certificate requests)
Search Using Serial Number Range or Request ID Range (certificates or certificate requests)
Search Using Certificate Status (Valid, Revoked, or Expired certificates)
After specifying your search, click the Go button to see a list of the results.
For all search results, OracleAS Certificate Authority displays 25 records at a time. To see more, use the Previous and Next buttons to navigate.
Use this section of the Advanced Search page to list certificate requests by status. From the drop down menu, select Pending, Rejected or Certified, and click Go. The list of certificate requests matching your status selection will display, 25 records at a time.
Use this section of the Advanced Search page to list certificates by a particular owner, which can be a server or an end-user. You can search by issued certificates or by requested certificates.
Table 4-2 Elements on Which You Can Search
| Element to Search on | Meaning/Content of that Element |
|---|---|
|
Common name |
The name on the certificate that you want to find |
|
Email address |
|
|
Organization unit |
Name of the unit within the company or organization to which the owner belongs |
|
Organization |
Name of the company or organization to which the owner belongs |
|
City/Locality |
The city location of the owner |
|
State/Province |
The state or province of the owner |
|
Country |
Two-letter code for the owner's country |
Use this section of the Advanced Search page to search for issued certificates (Certificate) or requested certificate (Certificate Request) by the distinguished name of the owner. You can enter the complete DN string instead of entering a value for each RDN string.
Use this section of the Advanced Search page to find all issued or requested certificates within a range of serial numbers. You can search by issued certificates or by requested certificates. Select one of those two choices, specify the lowest and highest serial number of interest, and click Go.
Revoking a certificate should make it unusable in your environment. Making the fact of revocation publicly available ensures that revoked certificates are not misused. Publishing the list of revoked certificates, called the certificate revocation list (CRL), accomplishes this goal because entities granting authentication can first check this list. For example, all the applications in your trust environment can use the CRL to prevent authentication of a revoked certificate.
Automatic CRL generation is enabled by default when OracleAS Certificate Authority is installed. Once you have provided the necessary email information, any failure of CRL generation causes an email to be sent to you automatically.
The first CRL is generated at midnight with a validity period (and regeneration interval) of one day. These values (and auto-generation) are configurable in the Scheduled Jobs section of the Notification subtab within the Configuration Management tab of the Administrator's web interface.
You can generate an updated CRL manually by performing the following steps:
From the main Certificate Management page, click the Update Certificate Revocation List (CRL) button. The Update Certificate Revocation List form appears.
For the CRL Validity, specify a number, representing how many days until the next update.
For the Signature Algorithm, choose from the drop-down menu, such as MD5 with RSA or SHA1 with RSA. (Oracle recommends using SHA-1 because it generates a larger digest, which is inherently more secure against known attacks, such as inversion and brute-force collision attacks.)
After filling in the form, click the Submit button. This action generates the CRL.
You can retrieve it for review or saving by choosing Save CRL then Install in Browser or Save to Disk.
The Oracle HTTP Server uses this list to check the validity of the SSL certificates it receives, rejecting an SSL connection with any end-entity whose certificate is on the CRL. If your system uses multiple such servers, you will need to copy the CRL to the appropriate path and filename used by those servers as their CRL. Follow the steps established for each server in setting up its CRL.
Similarly, browser and email clients can verify servers they are connecting to, verifying incoming S/MIME email using these CRLs.
OracleAS Certificate Authority publishes the following to Oracle Internet Directory:
Certificates are published to the user's directory entry in the attributes userCertificate and userSMIMECertificate
Certificate Revocation Lists (CRL) are published to the location cn=oca1,cn=CRLValidation,cn=Validation,cn=PKI,cn=Products,cn=OracleContext
|
Note:
|
This section addresses the following topic related to directory integration:
OracleAS Certificate Authority publishes the Certificate Revocation List (CRL), containing the list of revoked certificates, to Oracle Internet Directory. Other applications or users may need to work with the CRL from time to time.
You can obtain the CRL directly from the OracleAS Certificate Authority User home page, as explained in "Handling Certificate Revocation Lists (CRLs)" in Chapter 8.
Alternatively, for programmatic access, you can obtain OracleAS Certificate Authority's CRL using the ldapsearch command, which finds specific entries in the directory:
ldapsearch -p port -h ldaphost -b "cn=oca1,cn=CRLValidation,cn=Validation,cn=PKI,cn=Products,cn=OracleContext" –s scope -L "objectclass=*" certificaterevocationlist
where:
-p connects to the directory at a specified port
-h specifies the ldap host machine
-b specifies the DN location
-s specifies the search scope
-L prints the entries in LDIF format
"objectclass=*" indicates the search filter
certificaterevocationlist is the attribute to retrieve
For example:
ldapsearch -p 3060 -h rjackson-sol -b "cn=oca1,cn=CRLValidation,cn=Validation,cn=PKI,cn=Products,cn=OracleContext" –s base -L "objectclass=*" certificaterevocationlist
which produces the CRL output:
dn: cn=oca1,cn=CRLValidation,cn=Validation,cn=PKI,cn=Products,cn=OracleContext certificaterevocationlist:: MIICADCB6QIBATANBgkqhkiG9w0BAQUFADA8MQswCQYDVQQGE wJVUzEPMA0GA1UEChMGb3JhY2xlMRwwGgYDVQQDExNDQS1sa2V0aGFuYS1zdW4tOTA0Fw0wNTAxM DQyMjA2MjZaFw0wNTAxMDkyMjA2MjZaMCIwIAIBBRcNMDUwMTA0MjIwNTQzWjAMMAoGA1UdFQQDC gEBoFUwUzBRBgNVHSMBAf8ERzBFoUCkPjA8MQswCQYDVQQGEwJVUzEPMA0GA1UEChMGb3JhY2xlM RwwGgYDVQQDExNDQS1sa2V0aGFuYS1zdW4tOTA0ggEBMA0GCSqGSIb3DQEBBQUAA4IBAQAwBRgih GOB08sWRg2sIaelqLFlUYNvnbtOe4QjdyTPaAy6k31+15jGi1vA7UBw7c0HqLv9r9iHLn7x9MtBj Ei8GKj+OJ5GGvrVVnj7ngoSAfpMMhg805m+sgZu0UoBbBkuh9tyAGFzUbxqMCadwakUgEwi7OVsn 2jaDJilPD/1Lcp975hhlO0JH5hAwpERttSzaZcLqNEPGc9GMiAEUkTVCEa9rPwaw+C42msTZg38N 7hChaqVf6gj/NpwTOZw98tVyOfU/Iy5tndh5ghbx4PMQ8HoxjXuw0xh6VHTvjmV6q51eTfiAFD3e M+IWjxO7fdgL8zUTZ/6HA8fNxZgaJen
You can parse this output into a format suitable for your applications. If your applications require access to the CRL on a regular basis, you can set up an automated script to periodically copy the CRL to the file system.
OracleAS Certificate Authority and OracleAS Single Sign-On complement each other in simplifying the provisioning of user certificates and using them to enable PKI authentication to all applications that use OracleAS Single Sign-On. The two configuration choices described in this section can make this collaboration even easier:
Broadcasting the OracleAS Certificate Authority Certificate Request URL to SSO-Authenticated Users
Bringing SSO-Authenticated Users to the OracleAS Certificate Authority Certificate Request URL
The first configuration choice, broadcasting, makes it even easier for an OracleAS Single Sign-On user to file a certificate request than it is using the default OracleAS Certificate Authority configuration. OracleAS Certificate Authority's default is to provide certificates when an OracleAS Single Sign-On-authenticated user files a certificate request, a process that takes several steps. That process is described in the "Single Sign-on Authentication (SSO)" section of Chapter 8, "End-User Interfaceof the Oracle Application Server Certificate Authority".
Broadcasting makes it even easier by providing a link that can be sent to all users, enabling them to request an OracleAS Single Sign-On/OracleAS Certificate Authority certificate directly.
The second configuration choice is described in the section following that, Bringing SSO-Authenticated Users to the OracleAS Certificate Authority Certificate Request URL. It explains an OracleAS Certificate Authority configuration command that shortens that process considerably, by simplifying OracleAS Single Sign-On configuration. OracleAS Single Sign-On's default deployment does not automatically use SSL, which PKI authentication requires. So for OracleAS Single Sign-On to leverage OracleAS Certificate Authority-provided user certificates at run-time, OracleAS Single Sign-On server needs to be configured to use SSL and certificates. This second configuration choice, described in "User Certificatesand SSO Usage", details how this process can be further simplified, leveraging the usual configuration defaults.
The last two subsections are
They describe all the steps required for PKI authentication with OracleAS Certificate Authority and OracleAS Single Sign-On server, and the process Single Sign-On uses for authentication.
The URL at which OracleAS Single Sign-On users can get an OracleAS Certificate Authority Certificate can be sent by email, as an embedded HTML link, or published as a link in the enterprise portal. These methods give you flexibility in publishing this capability to users who may need it.
This URL, for the SSO Certificate Request, is
https://<Oracle_HTTP_host>:<oca_ssl_port>/oca/sso_oca_link
in which the sender of such an email should of course replace <Oracle_HTTP_host> by the web or IP address of the host, and replace <oca_ssl_port> by the Oracle Certificate Authority SSL Server Authentication port number.
For information about the host and port number in the URL, see "Requesting the Administrator Certificate", Step 1.
Users can then click this link and do the same steps detailed in the next section, Bringing SSO-Authenticated Users to the OracleAS Certificate Authority Certificate Request URL.
|
Note: If port changes have occurred since installation, then the most current information is not in portlist.ini. Instead, sign on to the Oracle Enterprise Manager Control and click the instance on which OracleAS Certificate Authority was installed. Then click the Ports link, find the entry in the Type column that says "OracleAS Certificate Authority Server Authentication (SSL)", and use the number in the adjacent column, headed "Port In Use". |
Although Oracle Application Server Certificate Authority is configured by default to act on OracleAS Single Sign-On authentication, there are several steps. Users would still need to go to the OracleAS Certificate Authority user interface, select SSO authentication, and then request the certificate. (See Chapter 8, "End-User Interfaceof the Oracle Application Server Certificate Authority", in the Single Sign-on Authentication (SSO) subsection.) Some users might find this process a bit difficult.
Therefore, OracleAS Certificate Authority has a mechanism to simplify the user experience, by sending users directly to the OracleAS Certificate Authority Certificate Request URL after authentication by the OracleAS Single Sign-On server.
Oracle Application Server Certificate Authority can be configured to provide this URL to OracleAS Single Sign-On, for display whenever OracleAS Single Sign-On is not using a certificate to authenticate a user. After OracleAS Single Sign-On authenticates such a user, it then displays the OracleAS Certificate Authority screen enabling that user to request a certificate. After that certificate is created and installed into the user's browser, future authentication can simply use that certificate automatically. (It should be noted, however, that this pop-up screen is shown to all users whether they are interested or not, and to some it could seem an inconvenience.)
To configure OracleAS Certificate Authority in this way, the administrator uses the ocactl command-line tool (with the administrator password) to issue the following command:
ocactl linksso
The administrator can also use the ocactl command-line tool (with the administrator password) to cancel the use of this URL through OracleAS Single Sign-On, by issuing the following command:
ocactl unlinksso
Please note that these commands do not require OracleAS Certificate Authority service to be shut down. However, the SSO server needs to be restarted for them to take effect, by using the following commands in the OracleAS Single Sign-On server ORACLE_HOME:
$ORACLE_HOME/opmn/bin/opmnctl stopproc type=oc4j instancename=oca $ORACLE_HOME/opmn/bin/opmnctl startproc type=oc4j instancename=oca
After the ocactl linksso command is executed and the OracleAS Single Sign-On server is restarted, the OracleAS Certificate Authority welcome page will be displayed whenever OracleAS Single Sign-On is not using a certificate to authenticate a user. That page looks like the following illustration:
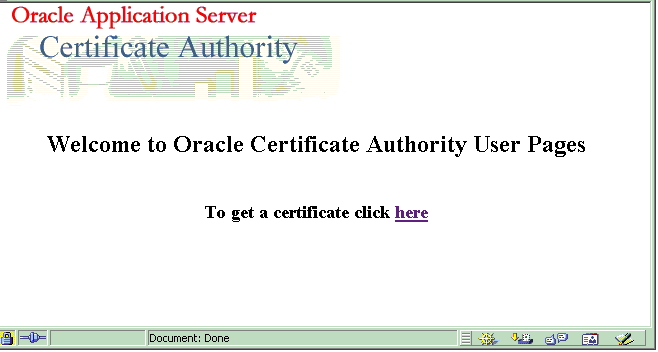
When the OracleAS Single Sign-On user clicks that here link, the OracleAS Certificate Authority certificate request page appears:
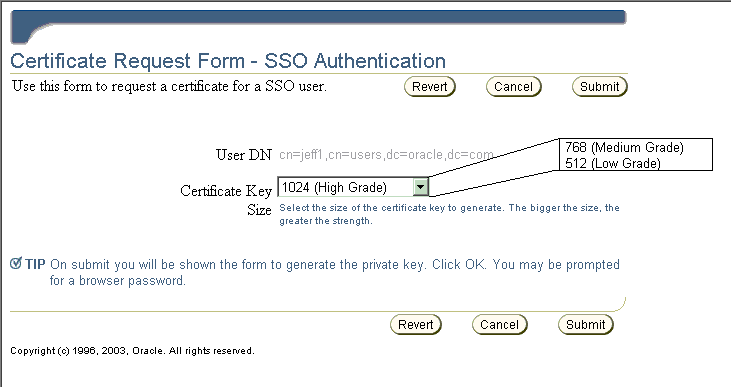
This composite illustration shows that SSO users must choose a key size and then click Submit once their choice is set as desired. (Clicking Revert changes the choice back to the default.) After the request is submitted, the key for this certificate is automatically generated (which can take a few minutes). Then the certificate is imported into Oracle Internet Directory and displayed to the user. After the user views the certificate information and clicks Install in Browser, the certificate is installed into the user's browser for automatic use.
After OracleAS Certificate Authority is re-registered with the Single Sign-On server, users who have already authenticated to OracleAS Certificate Authority using Single Sign-On can use their certificates as before.
New users can provision their certificates by using the OracleAS Certificate Authority Certificate Request URL for OracleAS Single Sign-On, as described in the sections referenced earlier.
Once OracleAS Single Sign-On can recognize a user by means of a certificate, she can access applications, including OracleAS Certificate Authority, either by username/password log-in or by certificate.
Thus, after a user logs in with username/password, follows the steps to create a certificate, and installs it into the browser, she can thereafter authenticate herself to the OracleAS Single Sign-On server through PKI.
When the browser of a user presents a certificate to OracleAS Single Sign-On, wanting authentication to use some application, OracleAS Single Sign-On checks that certificate against the directory. If the certificate stored under the user's nickname (and optionally his subscriber name) matches the one presented by the browser, the authentication is successful.
|
Note: Matching rules in Oracle Internet Directory control how certificates offered are matched to certificates in the directory. See the following references:
|
The single sign-on server then supplies the application with a URLC token containing user information, enabling the application to redirect the user to the requested URL. The requested content can then be delivered.
Table 4-4 lists the installation default values and other information, including default locations and validity periods for several important wallets.
If you want to change the depth of Sub CA's, that is, the path length, then the CA signing wallet should be regenerated using the command line. Use ocactl as described in Appendix A, "Command-Line Administration", in the section entitled "Generating a Sub CA Signing Wallet from OracleAS Certificate Authority".
However, once the CA is regenerated, all previously issued certificates would be invalid. So if you want to change the path length value, the CA signing wallet should be regenerated immediately after the install, as should all dependent wallets such as the SSL wallet.
|
Note: The OracleAS Certificate Authority schema in one repository can only be used with one OCA.When installing another OracleAS Certificate Authority, you must not choose a repository that has been used to install an earlier OracleAS Certificate Authority: the OracleAS Certificate Authority configuration tool will fail. This failure will force you to exit and restart the whole installation. |
Table 4-4 Installation Values for Wallets, CRL, and OHS Port (See Note 1.)
Notes to Table 4-4:
To set different properties, use ocactl.
For the CA signing wallet, used to sign the certificates, only the DN and Key Size can be changed during installation.
For the CA signing wallet, after installation all elements can be changed by running ocactl generatewallet -type CA to regenerate the CA signing wallet. You can also change the validity period by renewing this certificate with the desired validity period.
Used for the HTTP Server hosting the Certificate Authority. All CA SSL wallet values can be changed by running ocactl generatewallet -type CASSL. It can be regenerated at any time, such as expiration, with a commandline option, or replaced with an SSL wallet from a different CA, such as Verisign. This replacement can be done to avoid the warning "CA certificate not trusted" when first connecting to OracleAS Certificate Authority. Possible key sizes are 512, 768, 1024, and 2048, with 1024 the default.
$OH stands for $ORACLE_HOME, so the full location is $ORACLE_HOME/oca/wallet/ssl.
Other ports available for use with multiple installs, such as another OracleAS Certificate Authority, include 6602 through 6619.
$OH stands for $ORACLE_HOME, so the full location is $ORACLE_HOME/Apache/conf/ocm_apache.conf.
|
Note: Two listener ports are defined for OracleAS Certificate Authority in theocm_apache.conf file.
The reason two are needed is that there is a part of the functionality that does not need certificates and a part of the functionality that does need certificates. Using two listener ports is preferable to using the ClientCertificate optional directive in Apache, which would display a certificate-related dialog for all cases. |
You need to do certain steps to configure OracleAS Single Sign-On to use certificates. The full procedure appears in Appendix E, but without the detailed context and explanations provided by the Oracle Application Server Single Sign-On Administrator's Guide, which you should also read.
Here is an overview to the general steps you will perform:
Enable SSL as described in the Oracle Application Server Single Sign-On Administrator's Guide in Chapter 7, Enabling SSL.
Configure OracleAS Single Sign-On for certificates, as described in the Oracle Application Server Single Sign-On Administrator's Guide.
Re-register OracleAS Certificate Authority's virtual host to the Single Sign-On Server, as explained in the "Re-registering the Virtual Host with the SSL-Enabled SSO" section of Appendix E, "Enabling SSL and PKI on SSO".
After being PKI-enabled, the OracleAS Single Sign-On server can use certificates to authenticate users for applications rather than requesting username and password. When a user of an application partnering with OracleAS Single Sign-On chooses OracleAS Single Sign-On authentication, the browser asks her to choose a certificate to log in to those applications. The certificate she wants will be one previously installed into the browser. After she selects the appropriate certificate, the OracleAS Single Sign-On server will use that certificate to authenticate her and then redirect her to the partner application she originally requested.
This requirement presents the following issue:
Users need to log on to OracleAS Certificate Authority to get their certificates.
Since OracleAS Certificate Authority also uses the OracleAS Single Sign-On authentication service, users without certificates cannot log on to OracleAS Certificate Authority.
This issue is resolved by using multiple authentication levels in the OracleAS Single Sign-On server. Once PKI is enabled, all partner applications will have "medium high" security level (using certificates for authentication), even though OracleAS Certificate Authority can have "medium" security level by using username/password or Windows Native Authentication. This allows OracleAS Certificate Authority to use passwords to authenticate a user before issuing a certificate, but forces other OracleAS Single Sign-On server-enabled applications to use certificates for authentication.
See Appendix E for the full procedure, including those steps needed to configure OracleAS Certificate Authority to have "medium" security level using username/password. The steps specific to the security level are in the "Enabling PKI on SSO" section of Appendix E.
Similarly, OracleAS Certificate Authority can be configured to use other authentication mechanisms like Windows Native Authentication. Assign a security level to the plugin implementing the authentication mechanism and then assign the OracleAS Certificate Authority URL to use that security level as in Step 3 there (in "Enabling PKI on SSO").
|
See Also: For more detail, see Chapter 6, Multiple Authentication, in the Oracle Application Server Single Sign-On Administrator's Guide. |